Qantas is warning millions of customers that their personal data could be exposed after a cyber attack hit a third-party platform used by one of its offshore contact centers. Here’s everything we know about the breach so far. How did the breach happen? Qantas says it detected unusual activity on the affected third-party system earlier […]
Data security news & resources
Runtime data security vs DSPM
In the alphabet soup of cloud security tools, few acronyms have risen faster—or with more promise—than data security posture management (DSPM). Touted as a cure-all for sensitive data exposure, DSPM promises deep visibility into cloud environments. But as many CISOs have found, visibility alone isn’t enough. DSPM might show you where the problems are—but it […]

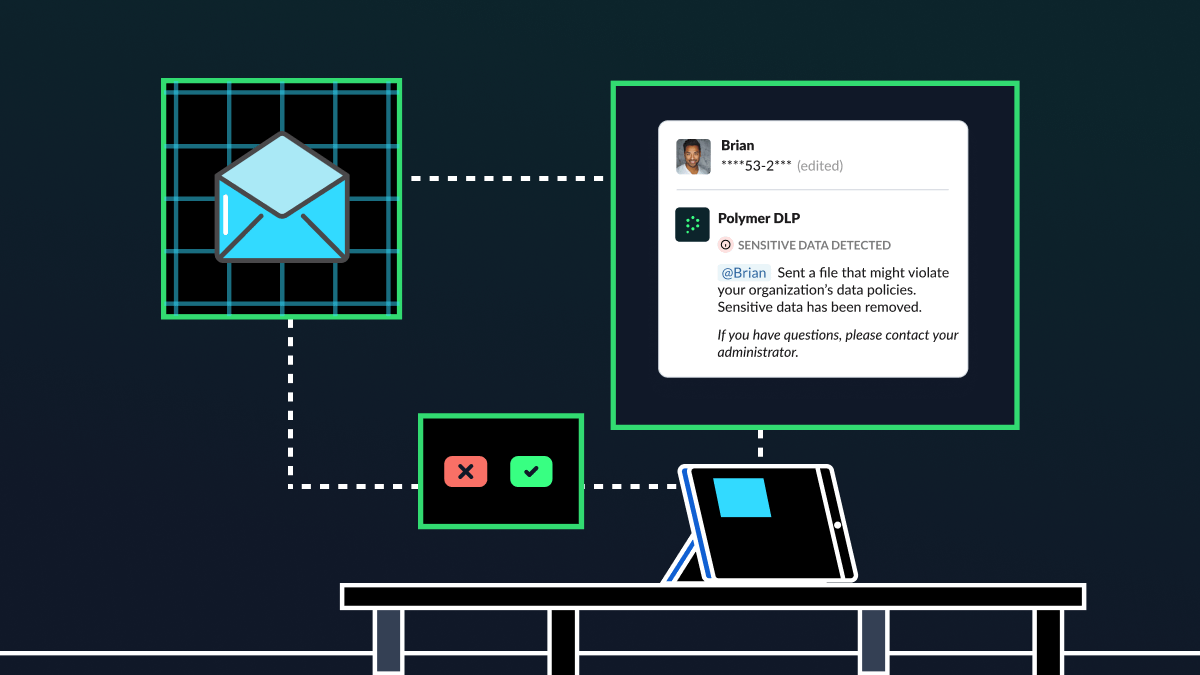
Is your customer service team a data leak waiting to happen?
On May 15, the crypto giant, Coinbase, announced that malicious actors had gotten away with the personal information of tens of thousands of customers—an incident set to cost the company nearly $400 million. But the scale of this breach isn’t the major story. It’s how the cybercriminals did it—bribing outsourced customer service agents to steal […]

Coinbase insider data breach: What we know so far
Crypto exchange giant Coinbase has confirmed a significant data breach involving bribed support contractors, compromised customer information, and a $20 million extortion demand. The attack is expected to cost the company up to $400 million in remediation and reimbursements—and it didn’t involve a single line of malware. Here’s everything we know so far. How did […]

Security training is failing. Here’s what really works.
Companies are pouring more money than ever into training their people to spot and stop cyber threats. But despite the investment, one stubborn issue won’t go away: humans are still behind the vast majority of data breaches. Even with security awareness training becoming the norm, the numbers show they’re having little impact—60% of breaches still […]

Overcoming supply chain risk with third-party management
In the past month alone, big names like Hertz, WK Kellogg, and DBS Bank have all reported serious data breaches. But these attacks weren’t the result of flaws in their own systems. Instead, attackers exploited weaknesses in their software supply chains—targeting third-party vendors to get in. This kind of breach is becoming less of an […]

Human risk management: the key to mitigating account takeover attacks
Account takeover (ATO) attacks are rising year after year, despite organizations investing heavily in multi-factor authentication. The reason? Cybercriminals’ tactics are evolving—and MFA is no match. Just take last month’s phishing attack targeting Microsoft ADFS. Hackers sent fake IT emails, tricking employees into logging into a cloned ADFS page. The moment victims entered their credentials […]

What are the security risks of DeepSeek?
The Chinese firm DeepSeek has officially entered the AI arena. When the company released its latest iteration in January of this year, it reached 16 million downloads in just 18 days—nearly double the 9 million downloads achieved by OpenAI’s ChatGPT at launch. Chances are, DeepSeek is already being used in your workplace, quietly boosting employee […]

DSPM vs CSPM: Why data security posture management is the future of cloud protection
As organizations move more operations to the cloud, security teams face a critical question: Is cloud security posture management (CSPM) enough, or do you need data security posture management (DSPM) too? The answer might surprise you. Understanding the difference: CSPM vs DSPM Cloud security posture management (CSPM) focuses on checking cloud infrastructure settings against security […]

SaaS security posture management: The missing link in your security strategy
Organizations are embracing SaaS applications at a lightning pace. But while these tools are excellent for driving collaboration and productivity, they also create significant blind spots in your security posture. With sensitive data flowing freely across platforms like Slack, Google Workspace, and Microsoft 365, traditional security approaches are simply no longer enough to prevent data […]

AI adoption and SaaS consolidation: Navigating security challenges in 2025
Today’s businesses are moving fast—AI adoption is skyrocketing, and SaaS apps are multiplying across teams. But with that growth comes a serious challenge: securing a tech stack that’s evolving faster than traditional security solutions can handle. The perfect storm: AI adoption meets SaaS consolidation As organizations embrace AI to drive innovation and efficiency, they’re simultaneously […]