Organizations are charging full-speed into AI adoption—eager to boost efficiency, outpace competitors, and unlock entirely new ways of working. For business leaders, the mandate is clear: move fast, or get left behind. But for security teams, the pace is less exciting and more alarming. Every new AI model introduces risks: more potential for data exposure, […]
Data security news & resources

Qantas data breach exposes six million customers
Qantas is warning millions of customers that their personal data could be exposed after a cyber attack hit a third-party platform used by one of its offshore contact centers. Here’s everything we know about the breach so far. How did the breach happen? Qantas says it detected unusual activity on the affected third-party system earlier […]
The agentic SOC: A near reality?
Burnout has been rife within the cybersecurity sectors for years. But, this year, it seems many SOC analysts have reached breaking point. With 71% reporting burnout and 64% considering leaving the cybersecurity field altogether, it’s clear that something has to change in the security operations center (SOC). The question is…what? Most CISOs are no stranger […]
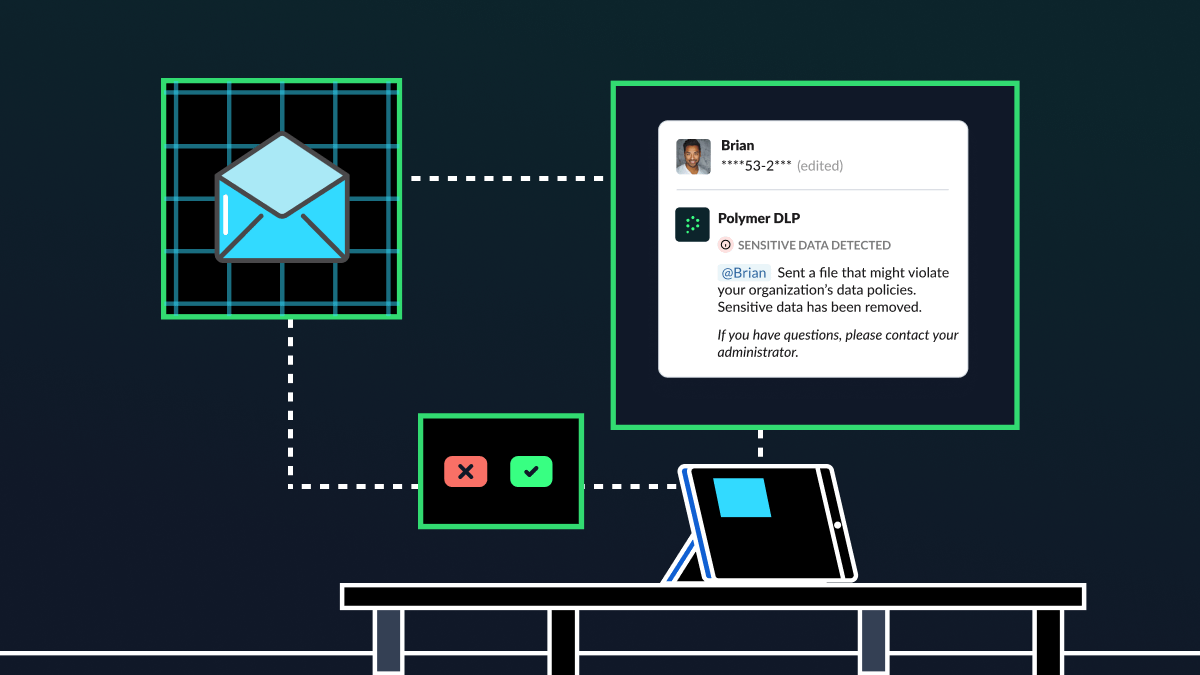
Human risk management: The key to a culture of cybersecurity
All employees make mistakes—whether that’s a typo in an email, sending a document to the wrong person or missing a deadline. Some mistakes, though, have greater consequences than others, especially when it comes to cybersecurity and compliance. Sending a sensitive document to the wrong recipient, for example, can be an immediate data breach and compliance […]
Runtime data security vs DSPM
In the alphabet soup of cloud security tools, few acronyms have risen faster—or with more promise—than data security posture management (DSPM). Touted as a cure-all for sensitive data exposure, DSPM promises deep visibility into cloud environments. But as many CISOs have found, visibility alone isn’t enough. DSPM might show you where the problems are—but it […]

Is your customer service team a data leak waiting to happen?
On May 15, the crypto giant, Coinbase, announced that malicious actors had gotten away with the personal information of tens of thousands of customers—an incident set to cost the company nearly $400 million. But the scale of this breach isn’t the major story. It’s how the cybercriminals did it—bribing outsourced customer service agents to steal […]

Why your business needs an AI firewall: Protecting data in the age of AI
The rapid adoption of AI tools across businesses has opened new doors for productivity and innovation. But these advancements bring significant risks. When employees use AI tools without proper safeguards, sensitive company data can leak into the wrong hands. This is where an AI firewall becomes essential. What exactly is an AI firewall? An AI […]

Security training is failing. Here’s what really works.
Companies are pouring more money than ever into training their people to spot and stop cyber threats. But despite the investment, one stubborn issue won’t go away: humans are still behind the vast majority of data breaches. Even with security awareness training becoming the norm, the numbers show they’re having little impact—60% of breaches still […]

AI and the new era of credentials theft
Despite what Hollywood might suggest, most data breaches don’t involve elite hackers cracking firewalls with lines of code. In reality, all it often takes is one stolen password. Just look at the Samsung breach last month—hackers used compromised credentials to access the personal data of over 270,000 customers. This kind of incident isn’t rare. In […]

Human risk management: the key to mitigating account takeover attacks
Account takeover (ATO) attacks are rising year after year, despite organizations investing heavily in multi-factor authentication. The reason? Cybercriminals’ tactics are evolving—and MFA is no match. Just take last month’s phishing attack targeting Microsoft ADFS. Hackers sent fake IT emails, tricking employees into logging into a cloned ADFS page. The moment victims entered their credentials […]

What are the security risks of DeepSeek?
The Chinese firm DeepSeek has officially entered the AI arena. When the company released its latest iteration in January of this year, it reached 16 million downloads in just 18 days—nearly double the 9 million downloads achieved by OpenAI’s ChatGPT at launch. Chances are, DeepSeek is already being used in your workplace, quietly boosting employee […]



