Today’s organizations are investing in cybersecurity controls and technologies more than ever before. It’s easy to understand why. Data breaches and compliance fines aren’t just inconveniences in the modern world of business. They’re potential points of failure. A wide scale security incident can completely erode customer trust and the bottom line, putting some organizations out […]

Navigating Zendesk vulnerabilities: Risks and remediations
In today’s ultra competitive digital landscape, businesses need to ace their customer service offering to attract, win, and retain customers. In fact, McKinsey research shows that investing in the customer experience (CX) can improve sales revenues by up to 7% and profitability by up to 2% in just one year. To enhance the CX, many […]

3 ways generative AI will impact CISOs in 2024
The role of the chief information security officer (CISO) has evolved tremendously in the last few years. No longer confined to the stereotype as the stern “office of no” guardian, today’s C-suite looks to the CISO as a digital business enabler, especially when it comes to balancing the risks and rewards of generative AI. However, […]

How to safeguard against ChatGPT vulnerabilities
In the year and a half since its launch, generative AI application ChatGPT has become one of the most popular in the world, amassing over 180 million users as of March 2024. What sets ChatGPT apart is its usability and accuracy. Through a simple prompt interface, the tool can address a diverse range of queries […]

Fujitsu malware hack: What we know so far
This week, Fujitsu, a prominent IT company based in Japan, announced the discovery of malware on its corporate network, which may have been used to gain unauthorized access to personal information belonging to customers or other parties. This incident adds to Fujitsu’s recent controversies, including its involvement in the British Post Office scandal. Here’s what […]

A comprehensive guide to Google Drive vulnerabilities
Organizations large and small rely on Google Drive and the Google Workspace ecosystem for a range of collaboration and document-based tasks. The cloud-based platform is highly intuitive to use and accessible from any device with the right login credentials, making it an excellent option for hybrid and remote teams. However, Google Drive’s usability can also […]

Unveiling Microsoft Teams vulnerabilities: risks and protections
Microsoft Teams is one of the most popular corporate messaging and file storage software platforms in the world, used by over one million organizations. But, like all software, Microsoft Teams is liable to vulnerabilities that threat actors can exploit. Just a few months ago, security researchers discovered a bug in Microsoft’s software that allowed them […]
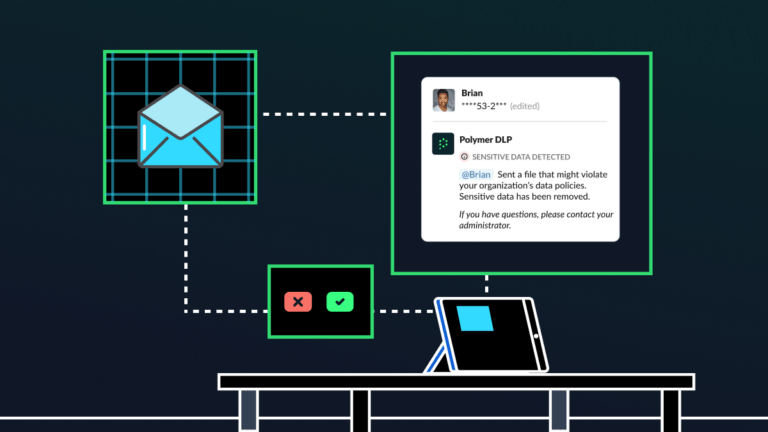
Elevating cybersecurity awareness training with AI-driven nudges
In 2024, human error continues to be the number one cause of data breaches, leaks and compliance fines in the enterprise. Despite organizations consistently investing in cybersecurity awareness training, something is going amiss: employees aren’t learning. For CISOs and their teams, the fallout of ineffective training programs can be severe. Many training initiatives are expensive, […]

Are you ready for the CPRA?
On March 29, 2024, the California Privacy Rights Act (CPRA) will come into effect, marking a new era of data privacy requirements for businesses operating in California. The CPRA aligns California’s data privacy regulations more closely with the European Union’s General Data Protection Regulation (GDPR), putting stringent expectations on companies regarding how they collect, use, […]

How DLP can accelerate NIS2 compliance
Medium and large organizations that operate in the European Union (EU) have just months to comply with NIS2, the EU’s latest and most stringent piece of cybersecurity legislation yet. Here, we’ll explore how data loss prevention (DLP) can help businesses meet NIS2 compliance requirements before the October deadline. Key focus areas of NIS2 NIS2’s requirements […]
Verizon insider data breach
Telecommunications and media giant Verizon suffered a data breach impacting over 60,000 employees after one employee gained unauthorized access to sensitive files containing personally identifiable information. How did the Verizon data breach happen? According to a data breach notification shared with the Office of the Maine Attorney General, a Verizon employee “inappropriately handled” a file […]

