In the past month alone, big names like Hertz, WK Kellogg, and DBS Bank have all reported serious data breaches. But these attacks weren’t the result of flaws in their own systems. Instead, attackers exploited weaknesses in their software supply chains—targeting third-party vendors to get in. This kind of breach is becoming less of an […]
Data security news & resources

Why data breach costs will reach new heights in 2025
In 2024, the average cost of a data breach soared to $4.88 million—a 10% increase over the previous year. This year, analysis indicates we will see the same percentage increase again, teetering over the $5 million mark. Obviously, this is an insane amount of money—an amount that would put many organizations out of business. So, […]

Generative AI and the future of master data management
Cloud adoption and SaaS tools have completely changed how organizations manage their most valuable data. It’s no longer enough to secure structured data that’s stored neatly in databases. The majority of your critical information—be it customer records, internal documents, or proprietary assets—is now unstructured, living in a vast network of file storage systems like Google […]
Landmark Admin data breach: Lessons learned
This week, Landmark Admin, an insurance administrative services company, disclosed that a data breach stemming from a cyberattack in May has affected over 800,000 individuals. In a filing with the Maine Attorney General’s office, Landmark reported detecting suspicious activity on May 13, 2024. In response, the company promptly shut down its IT systems and remote […]
Anatomy of the CrowdStrike outage: Lessons learned
Last Friday, a wave of digital disruptions swept across the globe as Microsoft users found themselves facing an unexpected and severe issue: their computers simply refused to power on. This seemingly small glitch spiraled into a global crisis, causing major television networks to go dark, disrupting air travel with mass flight cancellations, and forcing countless […]

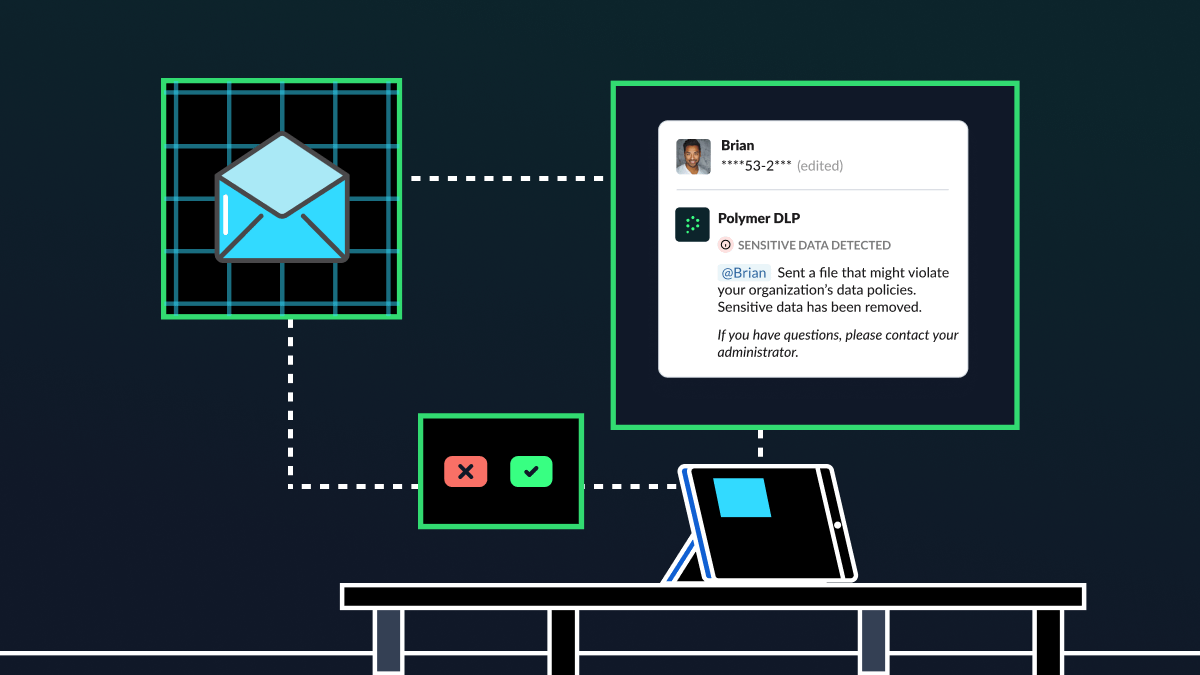
How DLP can accelerate NIS2 compliance
Medium and large organizations that operate in the European Union (EU) have just months to comply with NIS2, the EU’s latest and most stringent piece of cybersecurity legislation yet. Here, we’ll explore how data loss prevention (DLP) can help businesses meet NIS2 compliance requirements before the October deadline. Key focus areas of NIS2 NIS2’s requirements […]

What does the NIST Cybersecurity Framework 2.0 say about DLP?
The National Institute of Standards and Technology (NIST) has released the latest iteration of its renowned Cybersecurity Framework (CSF), designed to help organizations mitigate cybersecurity risk. The new CIST CSF 2.0 is aimed at organizations of all sizes in all sectors. What’s new in the NIST CSF 2.0? NIST initially released the CSF in 2014 […]

How to lower your cyber insurance premium in 2024
As the cost of data breaches rises year over year, many organizations look to cyber insurance to protect themselves from potential losses. Even in supplier contracts, more companies are now making cyber insurance a prerequisite to do business. However, cyber insurance is costly. Five years ago, obtaining coverage was easy and relatively cheap. But, today’s […]

4 questions CISOs need to consider before deploying generative AI
The boardroom conversations have begun. Your company’s CEO is eager to put generative AI into action. They know it’s vital to improving efficiency and productivity as well as maintaining competitiveness. But, they’ve also heard about the risks. Namely, hallucinations, data leakage and cyber-attacks. So, they turn to you: the company’s CISO. You, yourself, know that […]
NASA’s DLP program fails to lift off
Houston, we have a problem. NASA may have put men on the moon, but its privacy program is in need of some rocket fuel. That’s according to the aerospace agency’s Office of Inspector General (OIG), who recently reviewed NASA’s privacy program and found its data loss prevention (DLP) approach to be astronomically lacking. In an […]

Millions impacted by Dollar Tree supply chain breach
You might be confident in your cybersecurity posture, but if you don’t know how your suppliers approach data protection, you’re still at risk of a huge data breach. That’s precisely what happened to Dollar Tree. Over the weekend, the well-known discount retailer hit the headlines after falling victim to a supply chain cyber attack. And, […]