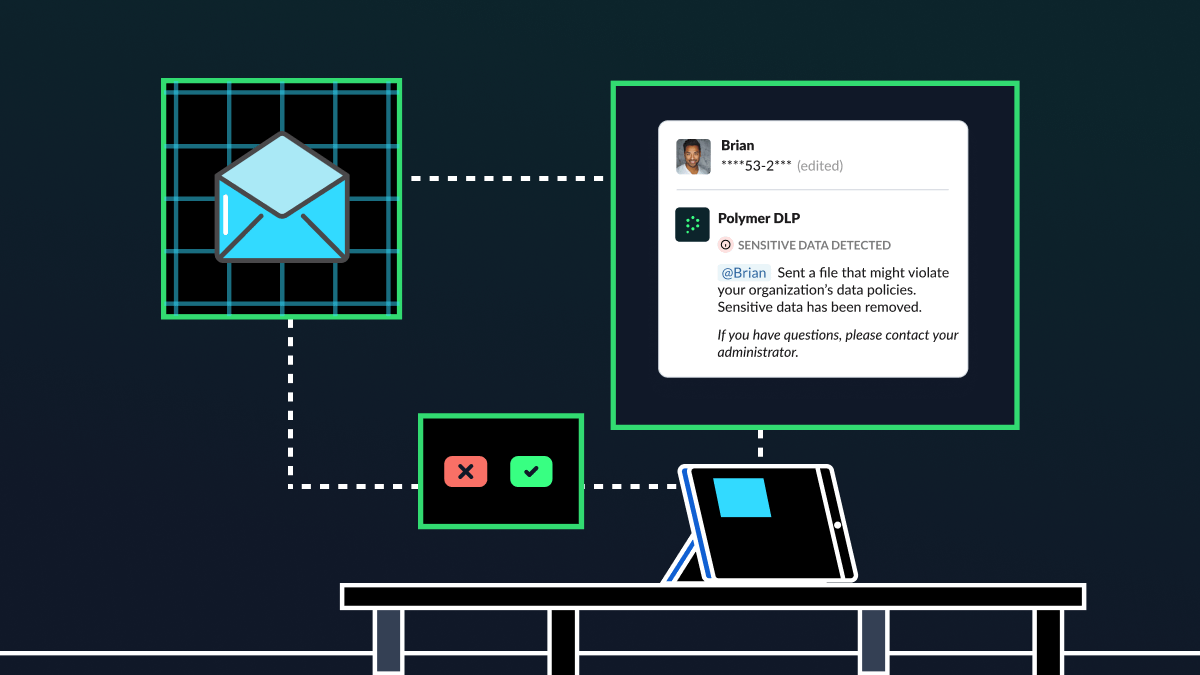
With over 4 billion people currently lacking access to healthcare services and a projected shortage of 11 million health workers by 2030, AI might well be a savior for healthcare organizations in the next several years. From revolutionizing drug delivery to enhancing diagnostic accuracy, AI could significantly enhance both the quality of care and the […]
Data security news & resources

Oracle Health data breach impacts hospitals across the US
ChatGPT said: Oracle Health is at the center of a major data breach impacting several U.S. hospitals and healthcare organizations. The breach, which originated from compromised legacy servers, has led to the theft of sensitive patient records. The attacker is now using ransomware to extort victims, demanding payments to prevent the stolen data from being […]

The hidden risks of data exfiltration in cloud and AI apps
Data is the engine of modern enterprises, powering everything from sales and marketing to HR, finance, and customer support. But as organizations increasingly rely on cloud applications and AI-driven tools to streamline operations, they’re also exposing themselves to an expanding array of data security risks. Sensitive information—customer records, financial data, intellectual property, and employee PII—flows […]

The complete guide to Dropbox and HIPAA compliance
With its user-friendly interface, seamless file sharing capabilities, and collaboration features, it’s no wonder Dropbox is one of the most popular cloud storage solutions on the market. Millions of businesses and individuals rely on this platform to store and access their files securely across different devices. Chief amongst these organizations are healthcare companies—medical providers, practices, […]

McLaren Health Care data breach impacts 2.2 million people
Does this headline give you a case of deja vu? That’s because, only last month, a ransomware group claimed to steal the personal health information (PHI) of 2.2 million patients registered with McLaren Health Care. However, it’s only now that McLaren is acknowledging the breach. What happened, and why the discrepancy? Let’s find out. What […]

How to overcome the regulatory risks of generative AI
The domain of artificial intelligence (AI), particularly generative AI (GenAI), is brimming with intriguing potential for companies all over the world. conversational AI bots, open-source large language models (LLMs), and specialized models are now ubiquitous in organizations. However, the rapid advancement and widespread adoption of these tools is creating substantial challenges when it comes to […]

What are the HIPAA Privacy Rule changes for 2023?
A little while back in December 2020, the Office of Civil Rights (OCR) issued a Notice of Proposed Rulemaking (NPRM), notifying us of upcoming augmentations to the HIPAA Privacy Rule. Three years and a lot of back and forth later, and it looks like those changes are about to be finalized into law. While we […]

How to protect patient data against insider threats?
It’s no secret that the healthcare sector is a prime target for cyber-attacks. Research shows healthcare organizations in the US experienced 1,426 attacks per week in 2022 – up 60% from the year before. But while healthcare companies spend their limited resources and time shielding patient health information (PHI) from external threats, they forget that […]

Over 4 million individuals impacted by Independent Living Systems breach
Miami-based healthcare software provider, Independent Living Systems, is in the hot seat this week, after announcing a data breach that impacted over 4.2 million individuals. The incident, which is the largest healthcare breach of the year so far, came to light on March 14, when the company shared an announcement stating it experienced an “incident […]

HIPAA compliance for Google Workspace admins
Under the Health Insurance Portability and Accountability Act (HIPAA), healthcare organizations must put in place specific controls to protect the confidentiality, integrity and availability of protected health information (PHI). However, complying with HIPAA today is much more complex than it was twenty years ago. As congress recently noted, “advances in electronic technology could erode the […]

Do covered entities need to retain HIPAA Audit Logs for six years?
“Is it true we need to retain our HIPAA (Health Insurance Portability and Accountability Act) audit log records for six years?” That’s a common question healthcare organizations ask us when they learn about Polymer data loss prevention (DLP) for HIPAA compliance. While our audit reporting capabilities enable you to capture records for well over a […]