US cannabis brand, Stiiizy, is in the spotlight this week for all the wrong reasons, after it submitted a data breach notification to California’s attorney general.
The contents of the filing detail a shocking data breach: an organized cybercrime group stole troves of sensitive data from the company in November 2024, getting away with confidential customer information that included driver’s licenses, passports, and medical cannabis cards.
Here’s everything you need to know, and the lessons learned.
How did the Stiiizy data breach happen?
While the Stiiizy incident is only coming to light just now, it actually has its roots in October 2024. According to Stiiizy’s filing, a malicious entity compromised the company’s point-of-sale (POS) processing vendor between October 10 and November 10 2024.
Specifically, the filing says: “We were notified by a vendor of point-of-sale processing services for some of our retail locations that accounts with their organization had been compromised by an organized cybercrime group.”
Note, we’ve bolded the word ‘accounts’ in the quote above—and that’s for good reason. But before we explain, let’s dive into exactly what sensitive data was stolen, and by whom.
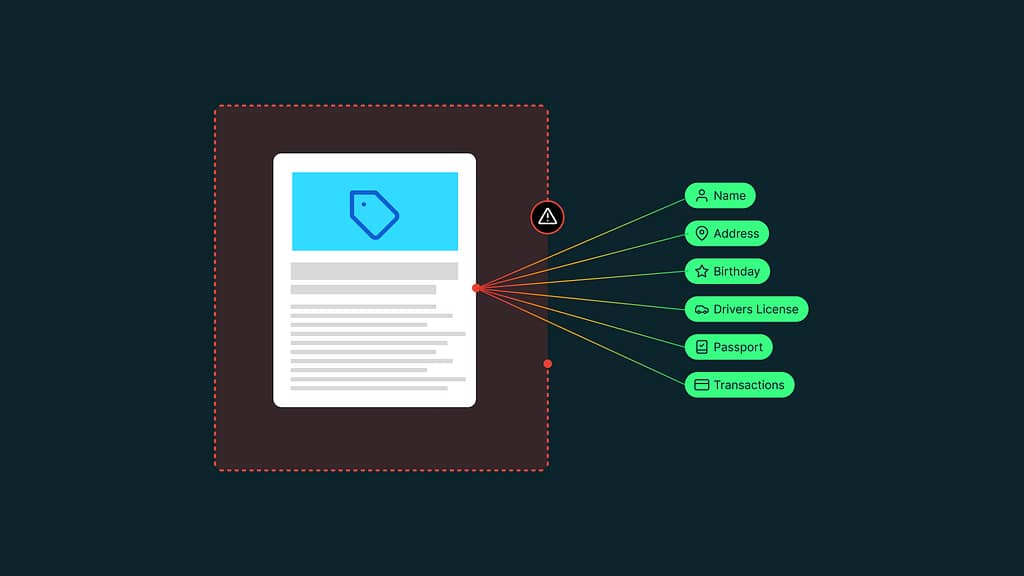
As Stiiizy’s filing explains, the cybercrime group extracted sensitive data that included:
- Names and addresses
- Dates of birth and ages
- Driver’s license and passport numbers
- Photographs and signatures from government-issued IDs
- Medical cannabis cards
- Transaction histories
So, who’s to blame? The cybercrime group, Everest ransomware, has stepped forward to take responsibility for the breach. They claim to have got away with the data of more than 420,000 customers. They also claim that they asked Stiiizy to pay a ransom in order to prevent the leakage of the files. It appears that Stiiizy refused.
Of course, this breach is a huge blow to Stiiizy customers. The plethora of data that has been stolen makes the perfect basis for highly realistic fraud and phishing attacks. Because of this, customers impacted are advised to monitor their financial accounts and credit reports for unusual activity, and set up automated fraud monitoring where possible.
Not just a POS problem
While the media has framed the breach as a point-of-sale (POS) issue, the devil really is in the details. As we noted earlier, Stiiizy has already emphasized that the breach stemmed from account compromise, not vulnerabilities in the POS system itself. This suggests the breach may not have even involved the POS directly. Instead, it’s likely that the attackers infiltrated the software-as-a-service (SaaS) platforms used by the vendor.
Though this remains speculative, we’ve seen this type of attack play out time and time again. Just look at high-profile cases like Uber, Cisco and LastPass—where attackers used similar tactics to compromise sensitive data through third-party platforms.
Here are two plausible ways the breach might’ve played out:
1. The attackers might have breached the vendor’s firewall and, once inside the network, targeted the vendor’s ticketing system to uncover employee credentials with admin rights. With these credentials in hand, the attackers could have escalated the attack, seeking out and siphoning off sensitive customer data.
2. The attack may have been painfully simple: a brute-force attack on the vendor’s cloud-based platforms, such as Slack or Microsoft OneDrive. Once inside, the attackers could have scoured through countless internal documents, slowly downloading sensitive customer information over a few weeks to evade detection.

Lessons learned
This breach is not a complex POS issue. It’s a cybersecurity problem that’s far more common—and thankfully, far more straightforward to defend against: attackers gaining access to SaaS accounts and using that foothold to exfiltrate sensitive customer data.
The real danger with SaaS accounts is their accessibility—attackers can access them from virtually anywhere, at any time, with the right credentials. While multi-factor authentication (MFA) can help reduce the risk of account compromise, breaches like the Twilio attack show how effective phishing tactics can bypass even the best identity and access management systems.
And who’s to say the worst is over for Stiiizy and its vendor? If attackers went undetected for 30 days, it’s entirely possible that the attackers are still at work from other compromised attacks, quietly siphoning off employee or customer information, undetected—until, of course, another ransom demand surfaces.
Prevent SaaS attacks with cloud DLP
To address these risks, the POS vendor—and really, any company reliant on SaaS systems—must reassess their approach to SaaS security. Identity and access management, while a valuable deterrent, are simply not enough on their own. Instead, companies need to move the focus from securing user identities to securing sensitive data at the source.
And that’s where Polymer data loss prevention (DLP) comes in. Polymer DLP is an AI-enhanced data security platform that mitigates the risk of sensitive data leakage and theft in SaaS platforms like Slack, Microsoft Teams and GitHub.
With Polymer DLP, even if an attacker successfully breaches an employee account, they still won’t be able to get away with sensitive data. The solution works by giving real-time visibility into user behavior and data movement across the cloud, utilizing a self-learning engine to build a deep, contextual understanding of user patterns.
Because Polymer DLP understands how legitimate users interact with data, it can easily (and autonomously) identify and block instances of account compromise in minutes—rather than the month-long window many organizations experience before detecting a breach. With our solution in play, for example, Stiiizy’s vendor would’ve discovered Everest Ransomware’s presence far earlier— before a data breach had a chance to occur.
Don’t become another breach statistic
Ultimately, SaaS platforms are the preferred playground for today’s cybercriminals. But many organizations are still catching up on the fact that SaaS apps need DLP just as much as networks and endpoints do.
So, let this incident be a lesson: SaaS apps are one of the most vulnerable, easy entry points for attackers. Native controls within these apps aren’t enough. You need a specialist, real-time solution specifically for SaaS that guards against data leakage and account compromise.
Protect your SaaS data now. Request a demo.










