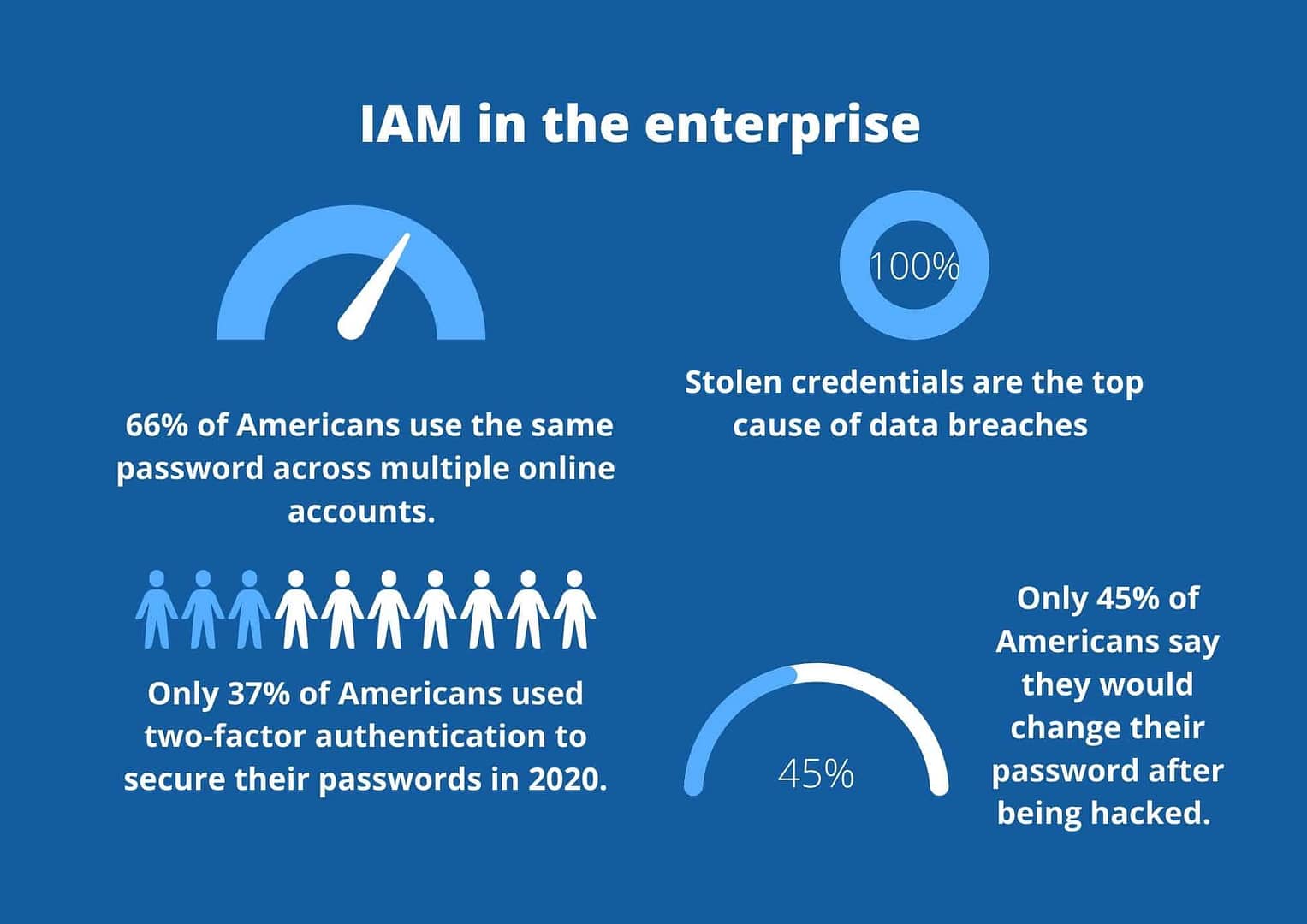
Verizon’s Data Breach Investigations Report found that stolen credentials were the top causes of data breaches for the fourth year in a row. In our hyper-connected, primarily remote, SaaS-dominated working world, email addresses and passwords are the lock and keys of employee productivity.
Unfortunately, though, if hackers get their hands on these details, they could steal a wealth of your sensitive company data.
Your organization needs an identity and access management solution to combat this threat–also known as (IAM).
What is identity and access management?
Identity and access management (IAM) is a process that helps you to define and control user roles and access rights within your company.
As Gartner succinctly puts it: Identity and access management (IAM) is the discipline that enables the right individuals to access the right resources at the right times for the right reasons.
IAM isn’t just a single solution; it’s a combination of technology and processes that holistically combine to ensure that authentic users can access the resources they need–nothing more or less.
Note, we used the word authentic above. This is the pinnacle of IAM: authenticating and authorizing users as they interact with corporate resources: cloud applications, on-premises infrastructure, folders, and more.
Moreover, IAM needs to look beyond just employees. Your customers, partners and suppliers will all need to be considered within your IAM solution.
The principle of least privilege
The IAM discipline is built around the principle of ‘least privilege’. In essence, this means that employees should only be able to access corporate resources relevant to their job role. A graduate employee, for example, shouldn’t be able to modify application configurations like an IT administrator would be able to.
Your IT administrator, and others like him, is considered a privileged user–someone who has elevated privileges. These users can modify your infrastructure and likely have unfettered access to sensitive data.
If one of these accounts is compromised, the fallout could be massive. In fact, Forrester estimates that a huge 80% of data breaches are connected to compromised privileged credentials.
You will need to make special considerations for privileged accounts within your IAM framework. They will need more rigorous monitoring, vetting and controls to prevent account compromise. This discipline is known as “Privileged Access Management (PAM). Standard features of PAM include:
- Keeping a real-time log of privileged accounts via user behavior monitoring
- Blocking suspicious actions through automation
- Mandating multi-factor authentication and single-sign-on for all privileged users
How to implement identity and access management in your company
With a thorough understanding of the principle of least privilege, you can go about creating an IAM framework in your organization.
Here is how to get started:
Separate individual users
One of the common security mistakes we see is teams using one login for a platform. For example, it’s typical for the sales team to have a team login for SaaS accounts. However, doing this undermines IAM. How can you tell who is who, if everyone is logging in from one account?
While it can be tricky to ensure your people don’t share login credentials, this is an essential security best practice. We recommend training your people on the risks of compromised credentials to drum home the importance of good password practices.
Mandate strong passwords
Passwords like 12345 and qwerty are a cybercriminal’s dream. In the age of LinkedIn, it’s easier than ever for hackers to do a tiny bit of digging about workout your company’s email address format.
If your people use basic passwords and use the same password across multiple accounts, your likelihood of a data breach skyrockets.
So, enforce these password best practices across your organization:
- Passwords should be a mixture of upper, lower and special characters – and numbers too!
- Use a unique password for every account
- Mandate that users change passwords at least every six weeks
- Incorporate a password manager into your employees’ workflows so they can keep track of their logins
Enable multi-factor authentication
At the very least, your privileged users must make use of multi-factor authentication. Ideally, though, you would make sure every user uses this solution. It’s a surefire way to reduce the likelihood of a successful credentials compromise attack.
Audit identities, access and user privileges
We live in a fast-paced world where employees come and go. You need to make sure that, when an employee leaves your organization, they lose their access privileges too. Ex-employees shouldn’t be able to access your Slack channels and other SaaS applications.
So, put an auditing system in place that enables you to review and update user access privileges regularly. This system should also consider changes in access privileges, based on factors like an employee being promoted.
Doing this manually can be time-consuming, but there are solutions out there to automate the process, making it intelligent and seamless.
Combine IAM with data-centricity
For enterprises, the complexity of IAM can be overwhelming. Even with the best intentions, IAM isn’t necessarily a foolproof solution. That’s why we advise complementing traditional IAM with data-centric access management.
In the cloud-first world, organizations need to identify access at an application level and at a data element level.
Each SaaS application brings a different set of usage patterns. Privilege access to data within these platforms is not only needed but essential as organizations grapple with privacy and data breach risks. This is where our platform comes in.
Polymer data loss prevention (DLP) relies on an autonomous platform that learns from historic usage patterns. This self-learning engine is then able to predict and prevent privacy violations before they occur, preventing data leakage and loss at the source.










