These days, everyone’s heard of ransomware. It’s touted as the most threatening form of cybercrime out there.
But, actually, it’s not. The FBI’s annual cybercrime report found that Business Email Compromise (BEC) attacks account for losses that are a massive 64 times worse than ransomware.
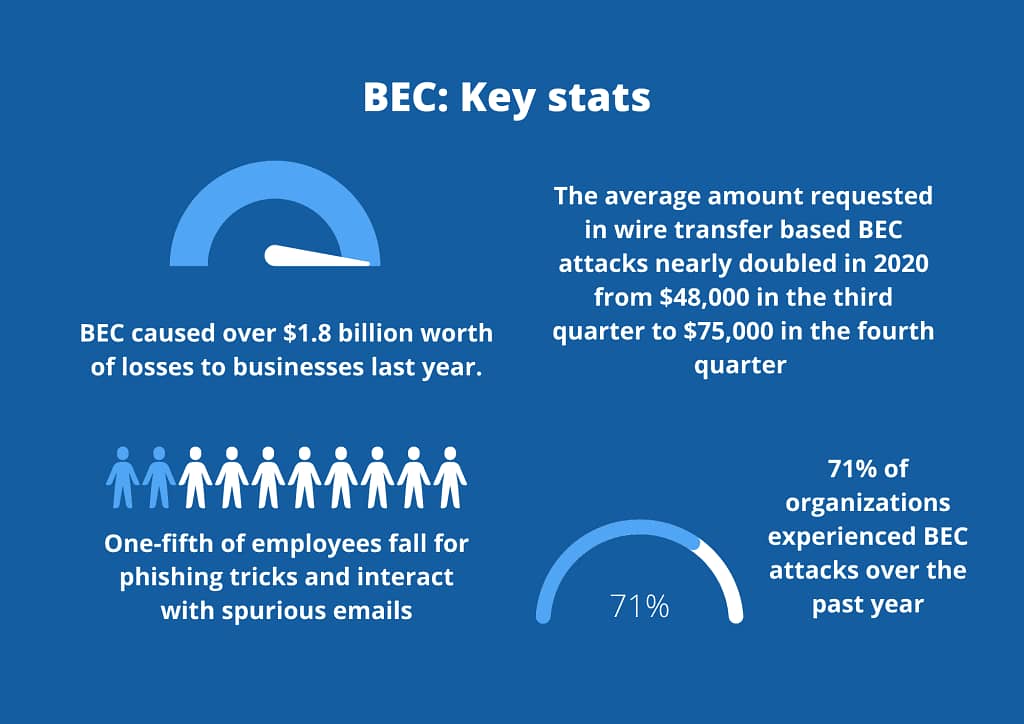
While ransomware contributed $29 million in losses, BEC caused over $1.8 billion worth of losses to businesses last year.
Read on to find out what BEC attacks are, how they work and how you can protect your company from becoming another statistic.
Definition: business email compromise attacks
BEC attacks are a highly-targeted cyber scam where criminals attempt to manipulate their victims into transferring funds or revealing sensitive information via email. Typically, the criminal will impersonate a trusted source–such as an employee’s boss or a company supplier–to make their requests for funds or data seem legitimate.
BEC attacks can be seen as a subset of phishing. However, while regular phishing attacks tend to be broad, generalized and, well, sloppy, BEC attacks are well-researched and personalized, so they are more likely to seem genuine to the victim.
BEC attacks rely heavily on social engineering tactics to trick their victims. A fraudster will do a lot of background research before sending this email to gain an understanding of:
- A company’s organizational hierarchy
- Who has purchasing power within the company
- Trusted suppliers and partners of a company
- Email addresses and personal details of employees
Armed with this information, hackers craft eerily realistic emails that persuade the victim at the employer’s company to send funds, purchase gifts cards or give away sensitive personal information.
They will spoof their email address to appear legitimate to the victim. Moreover, because the hacker impersonates someone with authority and usually adds a sense of urgency to the request, it’s more likely that the victim of the scam will oblige.
What is the purpose of BEC attacks?
Generally speaking, the purpose of a BEC attack will fall into one of the below three buckets:
- Financial: Verizon’s 2021 Data Breach Investigation Report found that most cyberattacks today are financially motivated. By aiming for wire transfers or gift cards, hackers can make a quick buck with a successful BEC scam.
- Account credentials: Some forms of BEC attacks ask employees to share sensitive login details, which can be used to breach the company network or applications and steal sensitive data.
- Strategic attacks: BEC attacks can be the first step in a strategic, long game for cybercriminals. Armed with employee credentials, attackers can then launch a more in-depth attack that directly penetrates the company’s infrastructure from the inside out.
The four types of BEC scams to watch out for
Ok, so we’ve covered what BEC scams are at a high level. Now, here’s an idea of what they look like in practice.
Here are the four main types of BEC scams to look out for:
- Fraudulent invoices: If you use foreign suppliers, watch out for fraudulent emails where cyber criminals pretend to be your supplier and say their bank details have changed. They’ll share an invoice and request funds to be transferred to their new bank account..
- CEO Fraud: A common scam we’ve seen in recent months is urgent emails from ‘Company CEOs’ requesting a junior employee to immediately purchase a large amount of gift card codes. The hacker will then ask the employee to share these codes over email and use them to their own advantage.
- Account Compromise: This is the scariest form of BEC attack out there. Rather than spoofing an email address, this attack actually compromises an executive’s email account and sends emails directly from it. These hacks can be extremely difficult to spot. Let’s face it, if you receive an email from an executive at your company marked ‘urgent’, you’re going to act, even if the request seems a little odd!
- Application impersonation: In these attacks, the victim will receive an email that appears to be from a SaaS application, like Zoom or Teams. Clicking the link will take the user to a fraudulent login page, where their details are then harvested for misuse.
How serious is BEC?
BEC is one of the most significant financial risks to businesses today. Unlike malware attacks, which are usually detected by antivirus, BEC attacks rely on human error and manipulation. Because these emails are highly targeted and appear genuine, they’re challenging to spot before it’s too late.
It’s no wonder, then, that BEC is causing havoc for businesses across the globe, as these statistics show:
- A recent study found that one-fifth of the surveyed employees fell for phishing tricks and interacted with spurious emails
- The average amount requested in wire transfer based BEC attacks nearly doubled in 2020 from $48,000 in the third quarter to $75,000 in the fourth quarter
- 71% of spear-phishing attacks include malicious URLs, but only 30% of BEC attacks included a link. Hackers using BEC want to establish trust with their victim and expect a reply to their email, and the lack of a URL makes it harder to detect the attack
How to protect your organization from BEC attacks
BEC attacks work through social engineering and manipulation as opposed to malicious software. Because of this, you need to take a human-centric approach to combat these attacks.
Here’s how to do it:
Employee training
Empower your users to spot phishing and BEC attacks. We recommend sharing granular advice on what common BEC attacks look like, so your employees can become more aware.
Your people should watch out for:
- Urgent, out of the blue executive requests: A sudden request from your CEO for $1000 worth of gifts cards should be treated with suspicion. Encourage your employees to authenticate such requests by picking up the phone or hopping onto Teams or Slack before taking any action.
- Requests to keep the communication secret: A cybercriminal impersonating a trusted contact will likely ask to keep the request confidential as not to raise suspicion. Create a policy within your company that no financial requests should be secretive.
- Requests that ignore company protocol: Most companies have established financial processes in place. If a request asks your employee to bypass traditional channels, it will likely be fraudulent.
- Phony email domains that are different to the sender’s addresses: Encourage your employees to check the sender address of suspicious emails. These attacks often use lookalike sender addresses that are slightly different to authentic email domains.
We encourage you not to treat employee training as a tick-box exercise. Lengthy, boring away days won’t inspire behavioral change in your people. On the other hand, training that integrates into your people’s workflow through nudges and prompts has a high effectiveness rate. We’ve written about this in more detail here.
Enable multi-factor authentication
Multi-factor authentication requires your employees to verify their identity at least twice before they log in to their account, typically through a password and phone code or password and email link.
MFA is useful for defending against EAC attacks. Even if a criminal gets their hands on your employee’s login details, they won’t have the extra verification credentials to log in to their account.
Create strict vendor and partner policies
We advise creating written policies for financial transactions that people in and outside your organization adhere to. That way, if you receive a request that goes against your usual policies, you’ll know now that this request is fraudulent.
As well as this, it would be best if you put a protocol in place so that your employees know how to raise the alarm should they receive a suspected BEC scam.
Configure cloud-based DLP
If a hacker steals your employee’s login credentials, you can bet that their next step will be to try and find sensitive data, and one of the first places they’ll look is your cloud applications.
This is why it’s so important to ensure that you proactively secure sensitive data that is shared in your cloud apps, so that, in the event of account compromise, your PII is still protected from theft. We’ve written extensively about how cloud-DLP works here should you like to learn more.