Did you know that 40% of ex-employees have admitted to stealing corporate data for their next role? Worse still, it’s estimated that 25% of departed employees still have access to company resources and data.
Here’s a hard truth. If any of your employees have left your company with sensitive data downloaded onto their personal devices, you’ve suffered a data breach. And if these people still have access to the corporate network, you could suffer many, many more.
This is why proper offboarding is so important. The process is much more than an HR activity; it’s vital to maintaining data security.
What is offboarding?
Offboarding is the activity of creating a formal separation between your company and an employee that has been fired, retired or handed in their resignation. From an HR perspective, the process is about knowledge sharing, ensuring the leaving employee leaves in good will and gathering feedback to improve company culture.
For the IT and security team, offboarding centers around decommissioning the individual from corporate accounts, files and networks, while maintaining data security and compliance.
Improper offboarding: the security risks
Below, we’ll look in more detail at the security risks associated with a poor employee offboarding process.
Data loss
Any files or resources your ex-employee creates for your organization are considered company property under law. However, people don’t always see it that way. If any employee has left your organization on bad terms or feels unfairly treated, they may seek to right these wrongs by deleting valuable information.
This is especially likely if the person still has access to the corporate network after they’ve formally left your organization. With their credentials still active, they could wreak havoc on your internal documentation, leading to irreparable data loss.
Data theft
A step beyond deleting data is stealing data. An ex-employee could download sensitive information to take with them to their next role, for example. The intentions here aren’t always malicious. Some employees simply want to move into their next role with confidence, and data relating to customers, prospects and suppliers will help them do just that.
However, regardless of the intent, stealing data means your company has suffered a data breach.
Compliance violations
Data breaches are particularly bad news today because of the maze of data privacy regulations companies must adhere to. Rules like the GDPR, HIPAA, CCPA, GBLA and more mandate organizations to take a strict approach to data security and privacy.
If your ex-employee gets away with troves of personal information, you’re immediately at odds with these regulations, which could lead to hefty fines.
Loss of control
Even if your ex-employee hasn’t set out to leak or steal sensitive information, you need to make sure that, when they leave your company, they haven’t taken any confidential data with them. This is because your IT and security team will no longer have any visibility and control over the ex-employee’s devices or data.
If their personal laptop or phone becomes embroiled in a cyber-attack, a malicious actor could get away with your company information – and you won’t even know it until it’s far too late!
Account takeover attacks
Speaking of malicious actors, another big risk of improper employee offboarding is account takeovers. Failing to decommission SaaS app accounts creates dozens of dormant user identities which are never used or checked on. A hacker could stumble upon one of these accounts, break into it, and carry out all sorts of nefarious deeds without being caught.
6 steps for secure offboarding
As you can see, employee offboarding is not something to be taken lightly. IT and security teams must work with HR departments to create a thorough offboarding process. Here’s how to do it in six steps.
Take a people-centric approach
When an employee leaves your company, it should be your priority to make the experience positive. This is more of an HR task than an IT one, but there’s undoubtedly a symbiotic relationship. Taking a people-centric approach will reduce the likelihood of bad feelings and malicious actions, such as data theft. Good communication, clear expectations and a well thought-out process will help to foster feelings of goodwill.
As part of the offboarding process, it’s also vital to communicate the employee’s departure with their colleagues. That way, employees can begin to siphon off sensitive information sharing with this individual, and will become more alert to potential signs of data exfiltration.
Retrieve corporate devices
Retrieving corporate assets is a vital part of the offboarding process. Some organizations choose to do this during the in-person exit interview, although it’s not always possible in hybrid or remote organizations.
If your employee works on the other side of the country or never comes into the office, you’ll need to establish a collection process for corporate devices. Ideally, this will be done immediately in the days after your employee has left the company.
Prevent data exfiltration
Data exfiltration is most likely to occur in the weeks leading up to your employee’s last day. Most commonly, we see it happen via file sharing and downloads in SaaS apps like Google Workspace, Slack, Dropbox and Teams. It’s extremely easy for employees to create, share and copy files in these environments.
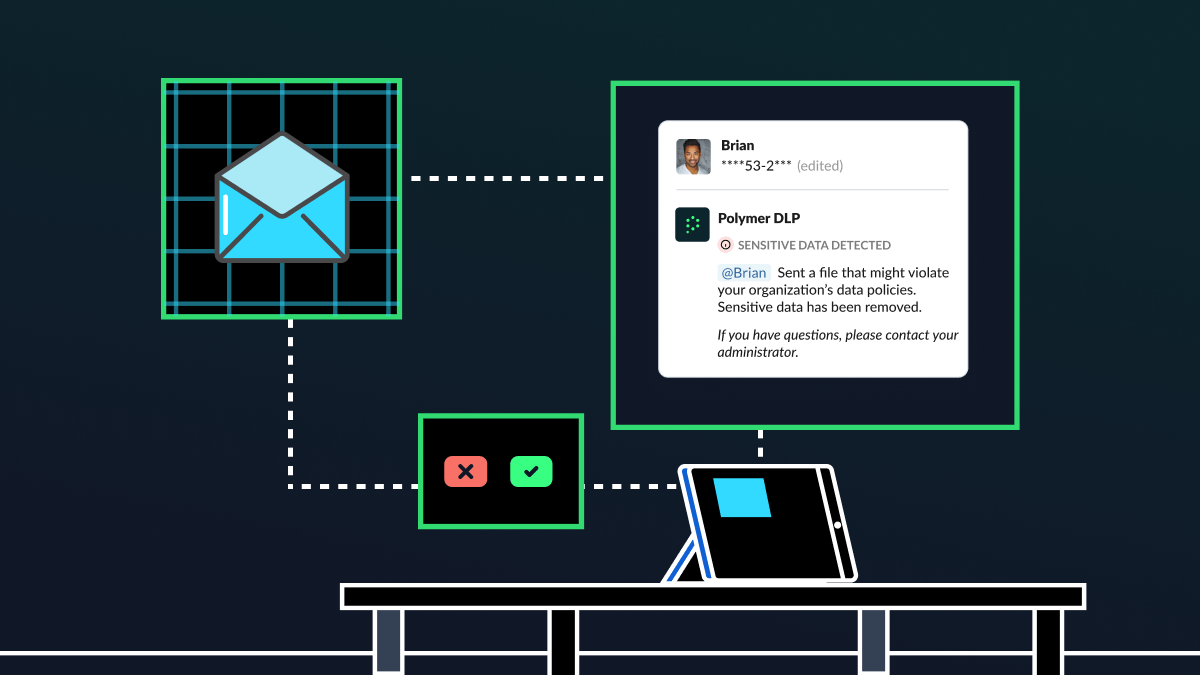
So, you need to put the right solutions in place to stop departing employees from exfiltrating this data from the cloud. This is where tools like cloud data loss prevention (DLP) come in. These solutions, like Polymer DLP, give IT teams visibility into how data is being used and shared inside cloud applications, along with the granular capabilities to block and redact data exfiltration before it happens.
Change shared passwords
A lot of organizations have team accounts for certain cloud applications. Because so many individuals use these accounts, you can’t decommission them after someone leaves. However, you should definitely update the shared password, so that the ex-employee can’t log back in after they’ve left.
Decommission email and other accounts
Half of IT leaders say that ex employees’ accounts remain active after their departure. As we’ve discussed, these formant accounts are particularly vulnerable to account takeover attacks, so it’s important to decommission them. However, in the process of doing so, you don’t want to lose valuable files that may still be stored in these accounts.
To overcome this challenge, you need a process for data migration. Polymer DLP can help you to discover sensitive information in these accounts, so you can more easily migrate to another individual or team’s accounts.
Don’t forget SaaS apps
While email tends to be the main focus during offboarding, SaaS apps like Slack, Teams and Google Workspace are just as—if not more—important. These apps are a treasure trove of unstructured, sensitive data. So, you need to revoke your employee’s access to these accounts on their last day.
Polymer DLP: the path to secure offboarding
Offboarding employees from SaaS apps can seem like an overwhelming task. Each application has its own unique settings, tools and processes, making the task of offboarding cumbersome and error-prone.
That’s where Polymer DLP comes in. Our tool empowers organizations to seamlessly offboard employees from SaaS apps while maintaining data security and compliance.