Whether you allow it or not, your employees are using their own devices for work purposes.
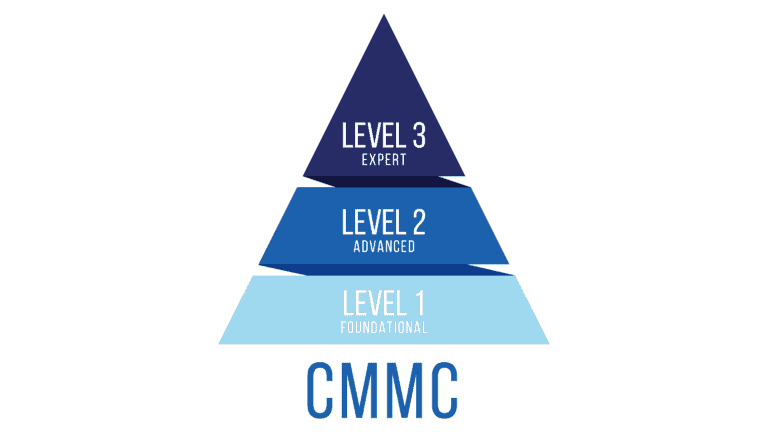
Do you need CMMC compliance? You will soon.
Use a data-centric approach to proactively prevent sensitive data exposure to third parties or vendors in our increasingly connected world.
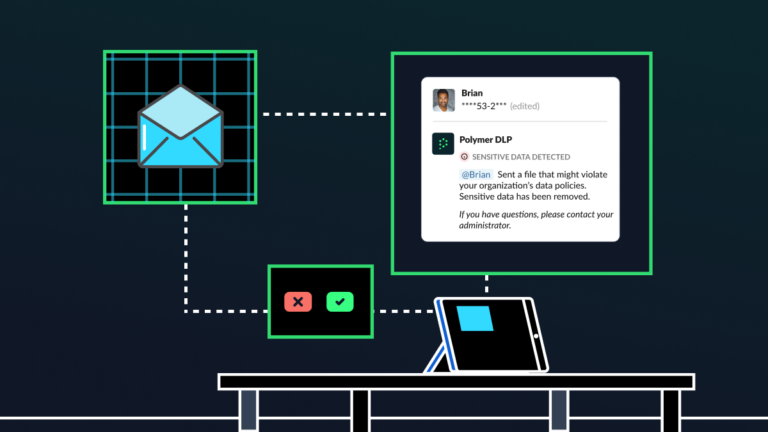
4 tips for training & enforcing data compliance
69% of employees have received cybersecurity training from their employers, yet 61% fail basic security tests. What’s going amiss?
Working with contractors? How to reduce your elevated data exposure risk!
External workers, freelancers and contractors add 3rd party risk of data exposure that should be acknowledged and acted on.

What is changing in ISO 27001 with 2022 updates?
ISO 27001-2002 has implemented 93 new controls spanning from threat intelligence to data governance controls. A higher bar has been set.

4 WFH mistakes employees make that put data security at risk
Remote work is exacerbating data security risks in general and specifically for SMEs. Employee training and a DLP reduces data exposure risk.

How a single faulty IAM policy can compromise a multi-million cybersecurity investment
IAM is the single most common failure point in tech infrastructure that can expose an organization to data breaches and ransomeware.

More investments in automation are required to combat the cybersecurity skills gap
Skill gap is a constant of this decade. Human-in-the-middle approach of many cybersecurity functions are not scalable. A rethink is required.

Why is DLP so important for Google Drive?
Google Drive’s focus on ease of collaboration also makes it ripe for accidental leakage or misuse of PHI, PII & HIPAA data.

Google Drive leaks: how do they happen and how can they be prevented?
SaaS DLP (Data Loss Prevention) – also known as a SaaS Data Exposure Prevention – is the best way to secure sensitive data in Google Drive

The top data security risks of Google Workspace
Top 6 google workspace security risks and how best to address them


