You’ve probably heard the phrase, “no man is an island.” We want to put forward the idea that no business is an island either. Think about your company. Chances are, you use several suppliers, partners and technology applications that you didn’t create in-house.
Inherently, today’s businesses are connected. All companies rely on third parties, and every third party depends on its own third parties. We can quickly see that one company is connected to a whole web of other businesses – even if they don’t realize it.
From a security perspective, third party risk is something organizations need to address. If a supplier or partner has access to your sensitive data and suffers a breach, you could face the repercussions – compliance fines, customer backlash and reputational damage.
Below, we’ll explore more about third party data breaches and give you handy tips on how to avoid becoming embroiled in one.
What is a third-party data breach?
Third-party breaches happen when a supplier either (i) accidentally leaks sensitive customer data to the public or (ii) is compromised by a cyber-criminal who steals sensitive data from their systems.
It’s very common today for suppliers to hold sensitive customer data. Many businesses outsource several functions to third parties, including tasks that deal with sensitive information like payroll, customer relationship management and work involving intellectual property.
While you might have stringent security controls within your own company, who’s to say that your third-party vendors take security as seriously? It’s commonplace for organizations not to know about their suppliers’ security strategies and solutions.
This lack of transparency is concerning – especially when we look at the prevalence of supply chain data breaches. Research indicates that a third (32%) of large organizations suffered attacks involving data shared with suppliers in 2021. Moreover, IBM found that third party involvement in a data breach increases the average cost from $370,000 to $4.29 million.
It’s also interesting to note that healthcare organizations, in particular, suffer at the hand of third parties. Research indicates that the healthcare industry was the most common victim of attacks caused by third parties, accounting for 33% of incidents last year.

How to tackle the risk of third-party data breaches
Supplier risk isn’t new. You likely have some risk management processes in place for suppliers – but these may not take security into account.
Obviously, ceasing relationships with suppliers isn’t an option for any company. Collaboration is vital in our economy. However, companies do need a way to ensure their data remains secure, no matter where it travels or where it resides.
To that end, we advise that companies adopt a zero-trust, data-centric approach to managing third-party vendors. This type of strategy centers around creating granular visibility into where data resides, and putting stringent, dynamic controls in place over who has access to it.
This type of approach not only makes sense for third parties, but it should be applied internally too. With regulations such as HIPAA, GDPR and CCPA now enforced, it’s more critical than ever for organizations to maintain control over their sensitive data, especially in instances where they’ve trusted their data to third parties.
So, how do you put zero-trust and data-centricity into practice? Let’s take a look below.
Identify your suppliers
A zero-trust approach to supplier management involves creating a map of your partners, so you understand who has access to what data. You can then implement tools like Identity and Access Management to ensure suppliers only access data legitimately.
Any data that is shared with third parties should also be automatically encrypted by default. This ensures that only verified users access your information, preventing an accidental data leak.
Classify your sensitive data
To protect sensitive data in third party environments, you have to know where it is. This is where data classification comes in. It’s a process of organizing data according to its type, sensitivity, metadata, and perceived value to the organization.
Use next-gen DLP
Once you’ve classified your data, you can implement a data-centric approach, which means using tools to secure data wherever it goes. When you collaborate with suppliers and partners, you likely use cloud applications like Slack, Teams and Zoom.
Traditional DLP solutions don’t protect your data in these applications. To secure your information in the hands of third parties, you need next-gen DLP.
Next-gen DLP or Data Loss Prevention (DLP) works by monitoring, classifying and protecting sensitive data across your cloud applications and collaboration tools. Through pre-defined policies, these solutions prevent data loss in real-time through automatic actions like redaction, encryption and deletion.
The best-in-breed cloud DLP solutions are also self-learning. They use AI to pick up on patterns about user behavior and sensitive data, and evolve their policies in line with this analysis. This takes the burden off IT teams having to re-define and set new data policies constantly.
Remember your auditing responsibilities!
Many of today’s data security regulations require rigorous reporting and auditing logs to demonstrate that data is secure. Ideally, your DLP solution will help this.
For example, our solution monitors, records and logs the journey of your sensitive data. Not only does this help you to make security improvements, but it makes the third party auditing process much more straightforward – the hard work is already done for you!
Take a holistic approach to third-party risk management
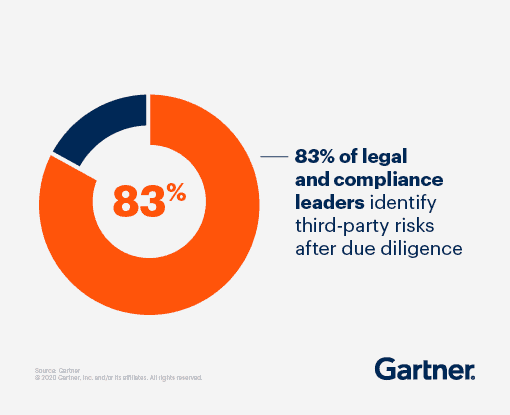
As well as deploying security tools to manage third party risk, it would be best if you looked at your internal processes. For example, Gartner found that many organizations don’t conduct due diligence until after they’ve committed to working with a supplier. This is potentially terrible news from a security perspective!
To that end, companies should look at the processes they have in place for onboarding, managing and reviewing suppliers’ security.
We advise organizations use NIST’s guidance on third-party risk management, which offers detailed advice for identifying and managing third party risks.
Our Data Loss Prevention (DLP) protects against data loss (DLP) on modern collaboration tools like Google Workspace, Slack, Dropbox, Zoom, GitHub, Jira, Zendesk and more with alerting & real-time redaction of sensitive and regulated information such as PII, PHI, financial and security data. Polymer DLP prevents sensitive data exposure across your SaaS apps without slowing your business.








