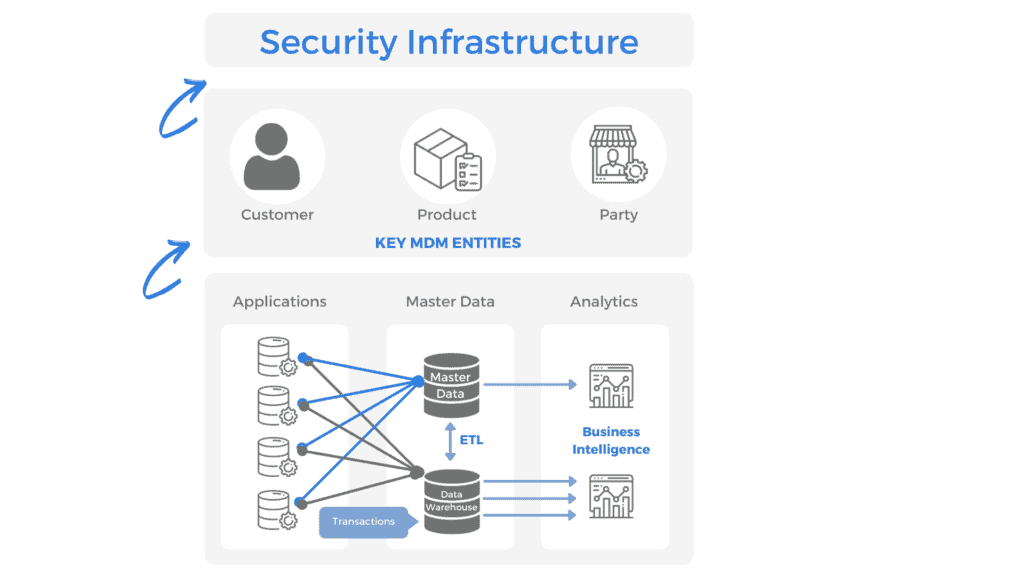
Building a security program without knowing what you are securing is a fool’s folly. An inventory of assets is a necessary first step towards a comprehensive enterprise risk program. Assets can either be physical (such as laptops, server racks, offices) or digital (software, data, reports).
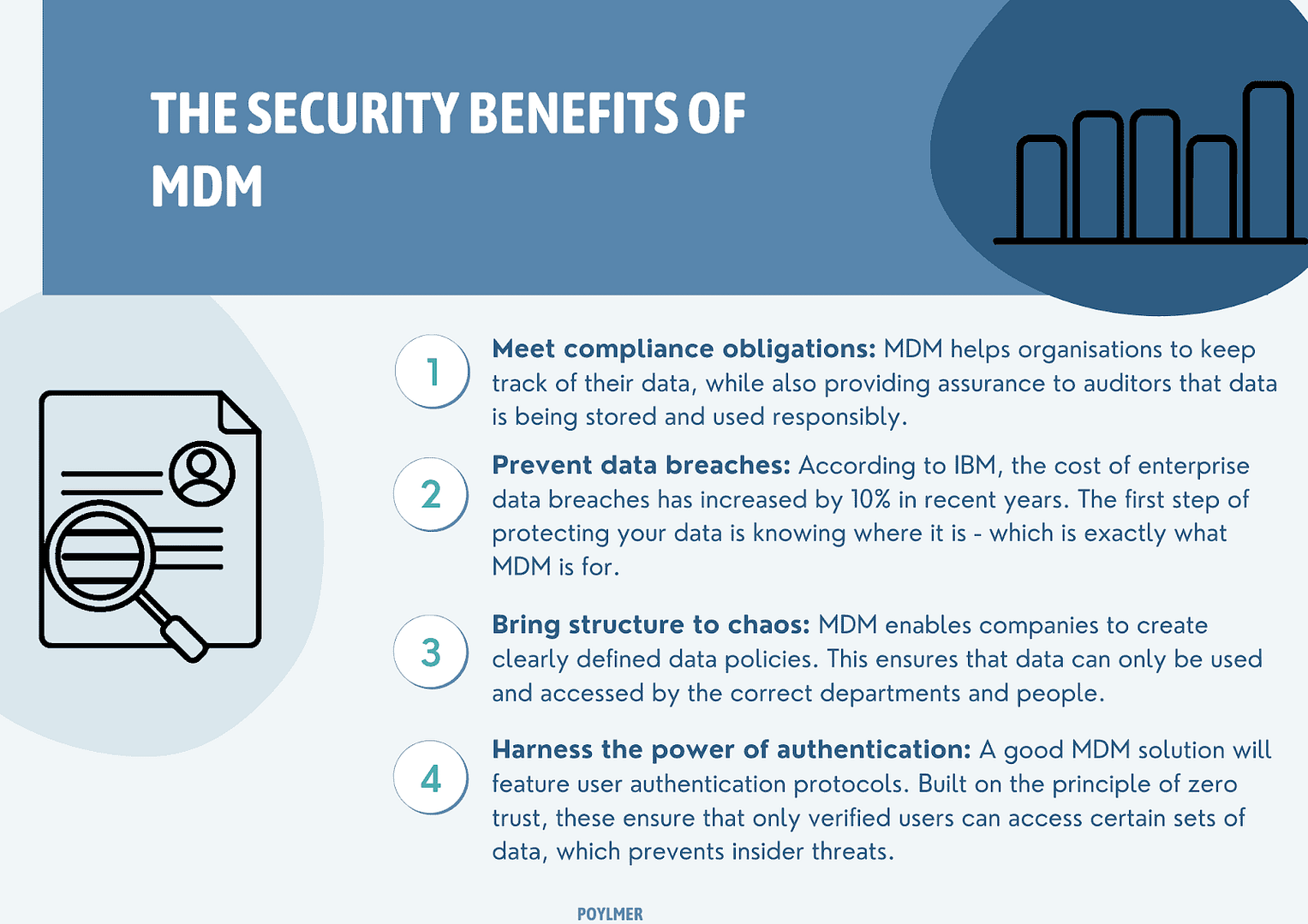
Master Data Management (MDM) is the methodology to catalog data assets and their corresponding relationship across databases, applications and object stores.