If you don’t have an incident response plan in place, then you need to create one ASAP.
An incident response plan, as defined by NIST, is a “set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber attacks against an organization’s information systems.”
Basically, your incident response plan is the rulebook that you follow in the event of a security incident. Having this plan in place helps your company to:
- Share out responsibilities, so people know how to act in the event of a data breach
- Respond to a breach more swiftly and efficiently
- Potentially reduce the damage of a security incident
- Keep calm and order in an unexpected event
While incident response plans are super important, research indicates that 77% of companies don’t have a formal incident response plan in place. There’s likely multiple reasons for this.
Many companies don’t have the in-house expertise to put together an incident response plan. Others are understaffed and some are burying their hands in the sand – hoping a data breach won’t happen to them.
Moreover, for those companies that do have an incident response plan, the plan itself is often outdated: built for yesterday’s security paradigm.
In today’s day and age, where so much company data is in the cloud, organisations need to have an incident response plan specifically for SaaS. However, creating this plan isn’t as simple as changing the phrase “on-premises” to “cloud” in your IR guide.
With its unique infrastructure and shared responsibility model, you will need to create an IR plan specifically focused on responding to security incidents in the cloud. Let’s explore this in more detail below.
Incident response in the cloud
NIST defines the incident response lifecycle as follows: Preparation, Detection and Analysis, Containment, Eradication, and Recovery, and lastly, Post Mortem. Coordination and Information Sharing is ongoing throughout the lifecycle.
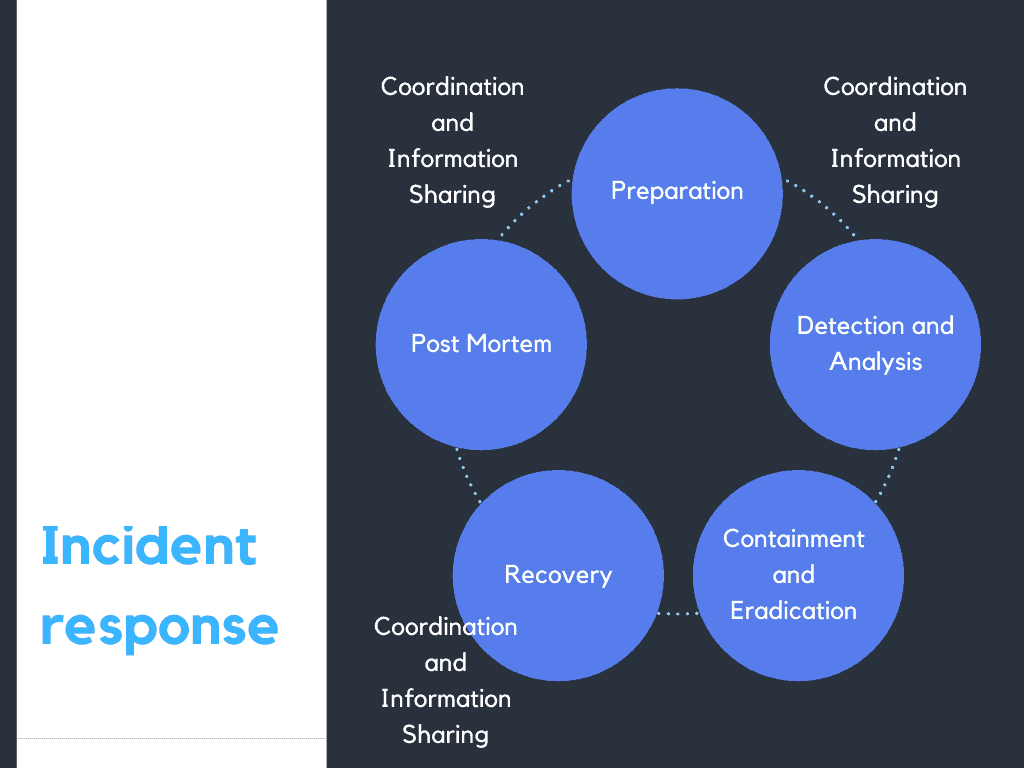
This lifecycle works great in theory but, in the cloud, most companies run into challenges – especially when it comes to detection and analysis.
If you think about the number of SaaS provider you work with, can you say – that you have deep, granular visibility into how your employees are using this applications? Do you know where your sensitive data is, at all times? And can you control where it goes and who has access to it?
If you answered no to these questions, chances are your SaaS incident response plan needs work. Incident response relies on visibility. If you don’t know that a data breach is happening, how can you stop it before it’s too late?
SaaS Security: It’s a case of when, not if
Many companies choose to hope that a data breach won’t happen to them. However, these days it is undoubtedly a case of not if, but when you will suffer a security incident. This doesn’t mean you will be hacked either.
While cybercrime is a risk, human error also causes a lot of cloud data breaches. In fact, Gartner thinks 99% of cloud data breaches will be the customers fault by 2025 due to human error.
The stats below highlight the risks of cloud data breaches:
- The latest Verizon Data Breach Investigations Report found that most cybersecurity incidents now involve cloud infrastructure.73% of security incidents involved external cloud assets.
- 32% of business-critical data now resides in SaaS applications. However, many companies lack the SaaS protection necessary to safeguard this data.
- According to IDC, 43% of organizations suffered unrecoverable data loss within the last 12 months, and 63% of organizations have suffered a data-related business disruption within the past 12 months.
- The highest ranked cloud threats are misconfiguration, unauthorized access, insecure interfaces and account hijacking.
- According to IBM, the average cost of a data breach is 4.24 million US dollars.
- 79% of enterprises want better integrated security and governance for their data in the cloud.
Resources for creating a SaaS incident response plan
If you want to get started with creating an incident response plan for SaaS, there are lots of useful resources and guides out there to assist you. We advise taking a look at the following:
- Cloud Incident Response framework
- SANS incident response in the cloud guide
- NIST Computer Security Incident Handling Guide
SaaS security best practices: lay the groundwork for incident response
A great incident response plan is useless unless you have the tools to give you deep, granular visibility into your SaaS applications. It’s crucial that you lay the groundwork for an effective IR lifecycle.
Here are some things to consider:
Third Party Risk Assessment: Before signing anything on the dotted line, you should analyze potential SaaS providers for risks relating the exchange of client data with the provider over a platform. No matter how small your company, a basic framework is hugely important in verifying your vendor’s privacy and risk posture. This is especially true for high growth fintechs, insure-techs and health-techs where customer data might be shared with external vendors. If your organization data is being accessed or shared with a SaaS provider in any shape or form, a Third Party Risk Assessment is highly recommended. The goal of any third-party risk management program is to reduce the likelihood of data breaches on the vendor’s side.
Account for the unpredictability of human nature: Your cybersecurity tools may be robotic, but your team members are humans. When you manage your teams you must be ready for potential errors. Inherently, human behavior is hard to predict and people may not always behave the way you expect them to. Unfortunately, in the cloud, these small mistakes can lead to big data breaches. So, consider thoughtful training defaults. For example, you can deploy a solution that nudges team members towards security-conscious behavior.
Implement a secure development lifecycle: Security and privacy are a way of thinking, and a practice that should be inherent to the way your team functions. One practical way to ingrain secure development is to put specific processes and activities in place that your team agrees to do every time software is updated or released.
Deploy a CASB 2.0: CASB 2.0s integrate with application programming interfaces (APIs). They are out-of-band solutions that integrate into cloud services, providing security and monitoring by maintaining a dialogue with other known APIs. These solutions give you the visibility that is essential to effective incident response. A CASB 2.0 will give you granular visibility into cloud application usage, including which employees are using cloud services, how they are accessing them and what information they are trying to upload, download and store in the cloud.
The best-in-breed of these solutions include access and authentication controls, which help you to manage cyber risks and subvert malicious actors trying to get their hands on your data.
Polymer DLP is a CASB 2.0 framework that protects against data loss (DLP) on modern collaboration tools like Slack, Dropbox, Zoom, GitHub, Jira, Zendesk and more with alerting & real-time redaction of sensitive and regulated information such as PII, PHI, financial and security data.










