A discussion moderated by Yasir Ali (founder, Polymer)
I recently moderated a panel for a TechGC webinar with 150+ leading general counsels in attendance. There was a lot of ground we covered on the topic of data governance and challenges in implementing it.
Following are some key takeaways relevant to any organization that is looking to either enhance or launch a data governance program.
Panelists:
- Talha Tariq (CISO Hashicorp)
- Samantha Davison (Privacy Robinhood)
- Liz Benegas (GC Totango)
- Moderator: Yasir Ali (Founder & CEO Polymer)
Oct 15, 2021 12-1:00 pm PT
What is Data Governance?
Any company collecting, processing or storing data requires accountability and framework of managing this data from acquisition to disposal. A data governance function requires different stakeholders from across the organization to adopt roles, responsibilities & policies for using and protecting sensitive information.
Defining ‘sensitive’ data or critical data elements can be tricky and one framework to think about it is looking at it as follows:
- Logical Data Elements: Refers to a grouping of data elements with a business connotation
- Physical Data Elements: Physical manifestation of the data elements like Name, Credit Card data found as database columns or within documents.
Applying these labels and constructing a mapping of the Logical→ Physical data elements across all data within a company’s environment could be the hardest part of implementing any governance program.
If customer records are found in multiple systems- Who is responsible for data privacy across the data stack?
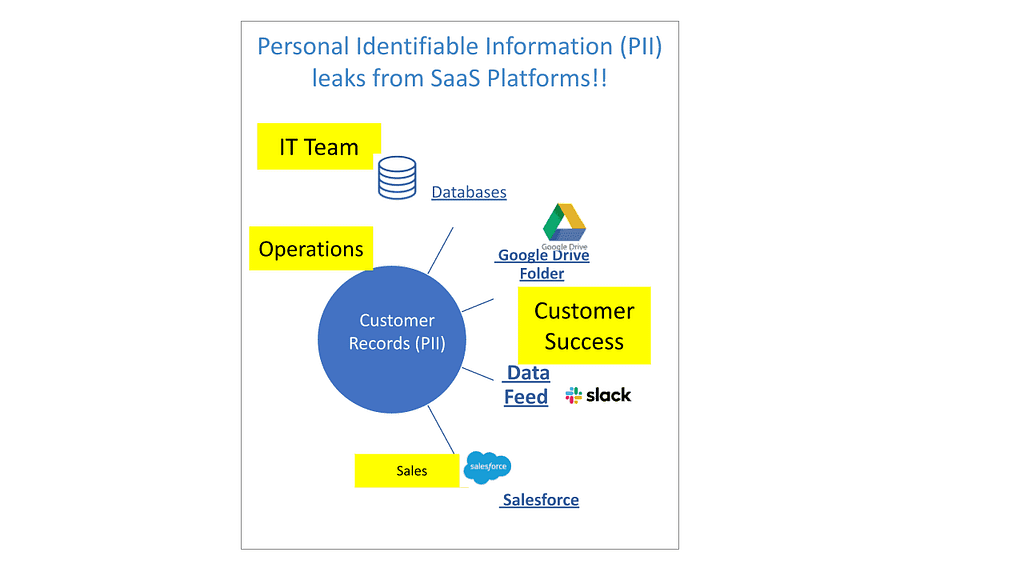
Who Owns Sensitive Data?
This gets even more convoluted when this data mixes with other data. In a ‘blended-data’ set, where does the ownership lie?
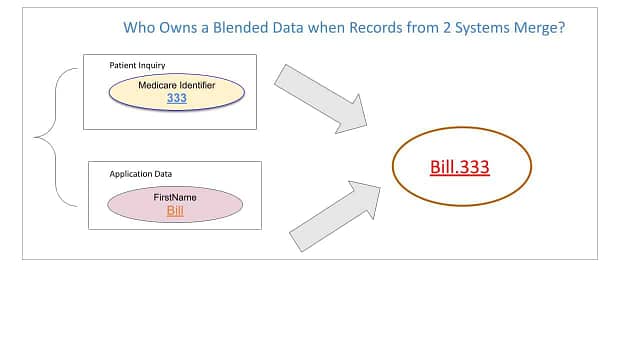
Talha calls for a dual ownership structure of data:
- Business
- Finance
- Marketing
- Operations
- Technical
- Database operators
- Engineers
This demarcation gets tricky when you have states of data that are ‘in-between’. For example log data from Systems can be this output which can have technical or business ownership.
From a General Counsel perspective, ownership of data is less relevant for Liz. She views data provenance from a liability standpoint and what risks a company underwrites in how it is handling this information. Getting this right requires a GC to be part of the executive function and defining what is truly sensitive data to be protected.
Privacy By Design
Samantha has implemented a cross-functional program to construct a privacy-aware organization. For example any new vendor being introduced by anyone in the organization is required to fill out a 10-15 point survey at the onset. This triggers a review where legal and engineering, in conjunction, with product teams will advise on the privacy implications of any new initiatives.
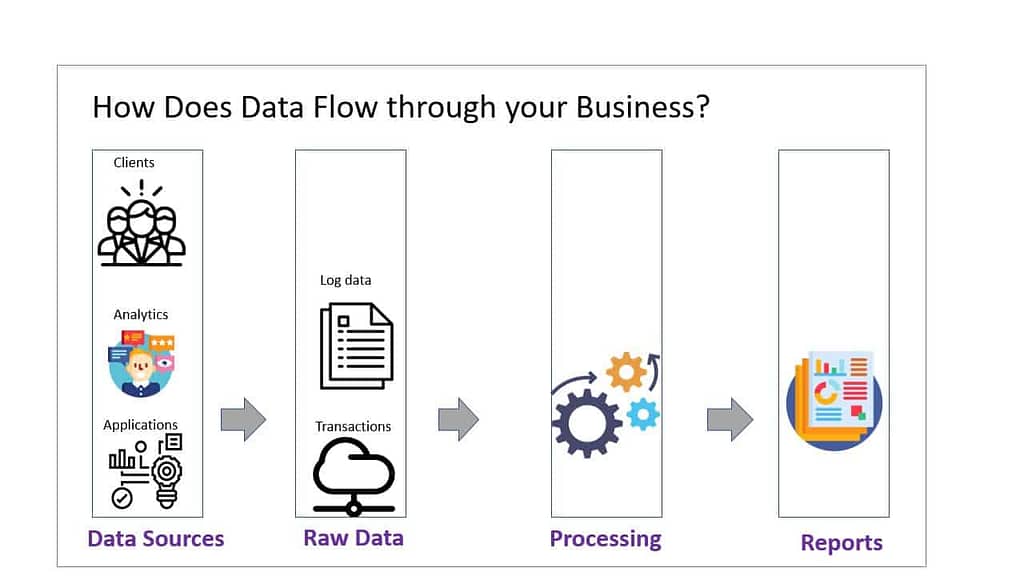
As multiple data inputs get transformed and reported on, who has the responsibility of keeping this data secure?
Robinhood takes a layered approach in mapping personal data across the whole environment. Any new product or major engineering project requires asking the following questions:
- What type of data is being used in this new initiative?
- What is the retention policy of this data?
- What infrastructure will be leveraged (or needs to be built) in storing and protecting this data?
Role of compliance and/or legal
For small legal and compliance teams consisting of 1 or 2 individuals, Liz recommends having a point person in engineering, product, people, security and other parts of the organization. A regular dialogue helps her be aware of product direction and be prepared for any major data flows being introduced in the organization. As a small team, there are only so many ‘fire-drills’ that can be pulled by her team and focusing on the most urgent compliance issues is the goal.
Contracts with vendors or third parties is a major source of focus for Liz. She is especially tuned to look for how Totango’s data is transmitted and handled by any partner that is brought on board. Some areas she is seeing a very rapid tightening of posture are:
- Verification of data controls as mentioned in the SOC2 or ISO report provided by the Vendor
- Effect of data protection practices related to HIPAA, GDPR, CCPA or other regulations if customer or patient data is being handled at all
- Analyzing any new relationship with the lens that if the counterparty is breached what risk does it pose on the company
Data mapping
Data mapping is a core construct in implementing a data governance program. Samantha goes by the policy of ‘You don’t know what data is leaving if you don’t know what it is’. Data mapping broadly can refer to following actions:
Data Mapping in a nutshell

At Robinhood she has developed a data mapping exercise based on defining, understanding and access to sensitive data. Talha follows a similar approach in defining sensitive data in 3 broad categories:
- Customer Data
- Corporate (Internal) Data
- Sales/Marketing/Operations Data
Any elements or physical data elements can be mapped across these broad categories. Having a super set of categories also streamlines the ease of mapping systems to business definitions of data types. This eases vendor qualification and managing such a program.
Vendor evaluation
Asking the tough questions upfront is the best policy. There are some basic security and technical hygiene requirements that are no-brainers according to Talha. A vendor product should have:
- SAML connectivity
- MFA
- SOC2
- Data Processing Agreement
A vendor assessment can also include a Privacy assessment that can be customized depending on what kinds of data is being shared/collected. A vendor/partner accessing customer data will of course have a higher hurdle to pass in this evaluation. DPA agreement or sub-processor agreements hugely important in defining the terms of engagement, especially within the EU.
Shortfalls of SOC2
SOC2 is a self-assessment and can be misleading in explaining the rigidity of security controls at the vendor or partner side. These controls are non-uniform and do not tell the full story of security risks. Talha jokes that a security assessment can conceivably say a person goes for a coffee and this makes the organization more secure. Liz focuses on getting evidence of these controls.
Instead of using SOC2 as a checkbox exercise, particular attention should be paid to what is being attested and verified. This helps at least provide some level of understanding in how comprehensive the attestation is.
Data governance and cyber readiness
Reducing the amount of sensitive data surface area over an organization’s systems is a crucial step in risk management. Data retention policies where not holding sensitive data beyond its ‘expiry’ data is also important in reducing the amount of information that an infiltration can leak.
Amount of data exposed on internal systems is directly proportional to the ‘blast radius’ of any breach. This can be an important forcing function in prioritizing data governance programs within organizations and a source of budget.
——–
Thanks TechGC for giving me the opportunity to put together this amazing forum that made this discussion possible. Look forward to having more such sessions in the future.
Please drop me a line if you have any questions or comments.
Yasir Ali, Founder/CEO Polymer
Linkedin: https://www.linkedin.com/in/yasirnyc/
Website: https://www.polymerhq.io/blog/
Email : yali@polymerhq.io









