In today’s digital world, a brand’s credibility is intrinsically linked to its ability to protect its data and IT infrastructure. This means that to maintain market share, keep customers satisfied and improve profits, choosing the right cybersecurity products is a must.
Deciding which cybersecurity solutions to use was once in the power of CIOs and CISOs but, as the stats below show, CFOs now also have a say:
- According to the Gartner 2020 Board of Directors Survey cybersecurity-related risk is rated as the second-highest source of risk for the enterprise, following regulatory compliance risk.
- By 2024, Gartner predicts that 60% of CISOs will establish critical partnerships with key executives in sales, finance and marketing, up from less than 20% today.
- According to Deloitte, 57% of CFOs are responsible for cybersecurity risks.
As data breaches and threats proliferate, CISOs and CFOs must work together to understand their company’s risk profile and implement the right security solutions at the right price. CFOs need to realize that cybersecurity is ultimately a financial issue. After all, data breaches can be a huge drain on the bottom line.
- The global average cost of a data breach is $3.86 million, according to the “Cost of a Data Breach Report 2020,” with the U.S. having the highest average at $8.64 million.
Buying consideration: point vs end-to-end security solution
Procurement of technology products in large organizations have spent considerable effort to reduce the number of vendors. In fact there has been a growing trend of cutting off smaller providers in preference to finding large end to end solution providers across.
On paper this reduced number of vendor line items makes the total cost of ownership of security products smaller. This immediate financial cost can be misleading. In reality a company might be taking on security debt by not going with the best-in-class solution in each of its defensive perimeter. After all, you’re only as strong as your recent vulnerability.
Zero day vulnerabilities and cloud misconfigurations of newer products puts organizations at risk in myriad different ways. No technology vendor in the market can conceivably protect an organization strongly across all risk surface areas.
Whichever approach is adopted, your first job is to not just look at the expense and the number of line items in assessing efficacy of security products. Rather, a thoughtful discussion with your tech and security teams is needed in designing a fault-tolerant infrastructure and the vendor discussion coming in later.
Addressing the challenges of cybersecurity ROI
Many CFOs struggle to quantify their company’s cybersecurity investments. It’s far too easy for cybersecurity to become a bottomless spending pit. Just look at how much spending has increased over the last few years, only for successful cyber attacks to be on the rise too.
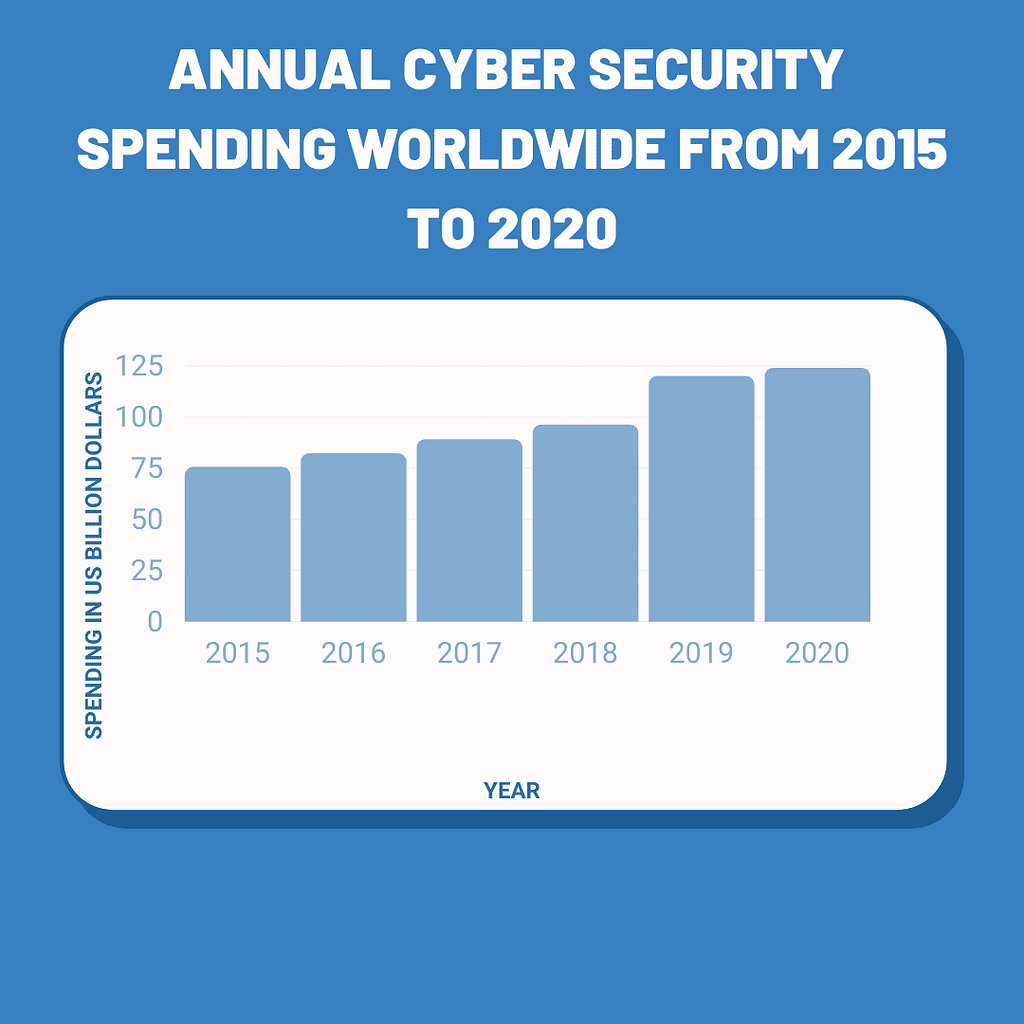
Spending on cybersecurity is showing no sign of slowing either. As the below stats show, the market is blossoming, as more and more vendors, startups and incumbents roll out new solutions.
- Enterprises are predicted to spend $12.6B on cloud security tools by 2023, up from $5.6B in 2018, according to Forrester.
- 61% of companies are increasing investment in cyber/information security this year, says Gartner.
- The global cybersecurity market is currently worth $173B in 2020, growing to $270B by 2026.
The amount of solutions out there can be overwhelming for CFOs. It can be difficult to know what they need, what works and what doesn’t, and whether their investments are providing a good return.
To move forward with confidence, CFOs need to measure cyber security investments to make sure they are providing value. They should do this both during the procurement process, as well as reviewing their current investments on an annual basis to make sure they are fit for purpose.
How to measure ROI when making purchasing decisions
CFOs must remember that cybersecurity investments won’t bring about increased revenue. Instead, these investments are focused on preserving capital and assets, and mitigating financial losses.
To help CFOs calculate ROI when making purchasing decisions, the SANS Institute has designed a specific calculation for cyber security – called Return On Security Investment (ROSI).
The calculation involves the following equations:
Annualized Loss Expectancy (ALE): An estimate of the amount of money lost in a single security incident multiplied by the estimated frequency that a threat will occur within one year (annualized rate of occurrence).
Mitigation Ratio: A figure based on the predicted number risks that would be mitigated by the solution you are considering. For example, if you are considering purchasing a solution that will reduce data loss risks by 90%, then the mitigation ratio is 90%.
Cost of Solution: The cost of the solution in question, including the upfront price, implementation and any maintenance costs.
While the ROSI equation only provides an estimate of the return on security investments, using the model consistently can help companies to understand how different solutions compare when going through the procurement process.
How to measure the success of a security product after a year or more
Implementing a metric program for security investments is essential to understanding what investments are working well – both from a financial and security perspective – and what solutions may need to be updated.
It’s recommended that CFOs and IT teams collaborate to implement the following metrics, and that they are reviewed at least annually – but preferably more regularly, say quarterly, to catch issues before they cause any damage.
The volume of incidents
Keeping a record of the number of security incidents within a company can help CFOs to understand any issues and blindspots within their security program. For example, a low number of incidents may indicate that the company’s cybersecurity solutions are effective. Furthermore, a decreasing number of incidents after a new solution has been introduced would indicate the same. However, if the company experiences an upward trend of incidents, then it’s likely that their solutions need to be reviewed and are not working as well as desired.
It’s important to note, here, that the measurement of incidents relies on accurate, complete, real-time data. The CFO will need to coordinate with the IT team to understand how to put the measurement framework into place. Ideally, they should take advantage of automation tools to make the process a light lift for their colleagues.
The time to detect a breach or data loss
According to IBM, the average time to identify a breach in 2020 was 228 days. This is not a state companies should be aiming for. Over a half year is more than enough time for cyber criminals to do immense damage, and compliance regulations such as the GDPR and HIPPA allow data protection authorities to give out hefty fines of up to 4% of a company’s annual turnover for these kinds of breaches.
With this in mind, CFOs should regularly inspect and quantify the average time it takes for the security team to identify an incident after it first occurs. The longer the time between the start of the incident and it being detected, the greater the need for security tools to help with data protection, threat detection and response.
The cost of malware attacks
Security incidents are a devastating cost drain. For example, the recent Kaseya ransomware attack cost the company weeks of downtime, as well as potentially damaging the company’s relationships with its clients and partners.
By measuring the cost of attempted malware attacks and security incidents, CFOs can gain an understanding of how well their security tools are performing or underperforming. When measuring these costs, it’s important to take into account the cost of downtime, the amount of resources needed to remediate the incident, as well as any costs incurred from compliance fines and public relations management.
If the cost of breaches is consistently low, then the CFO can begin to build confidence in their security tools, as these metrics show that the tools are doing exactly what they are meant to: protecting sensitive company data from malicious actors and accidental loss.








