In early January 2026, millions of Instagram users around the world woke up to unrequested password reset emails. This wave of notifications, which came directly from the platform’s legitimate systems, prompted major confusion amongst users; is someone trying to hack my Instagram account? Here’s what we know so far. Was Instagram breached? Since the emails […]
Data security news & resources

Update: LastPass fined £1.2 Million: A costly reminder to strengthen security
The UK Information Commissioner’s Office (ICO) has fined LastPass £1.2 million for security failures tied to its 2022 breach—nearly three years after attackers first gained access. The message is clear: data protection failures don’t expire when headlines fade. Regulators are still watching, and accountability can arrive long after the damage is done. For security leaders, […]

Update: Qantas breach escalates as hackers leak stolen customer data
When we first covered the Qantas data breach in July—in which up to six million customer records were accessed via a third-party contact center platform—it was not yet clear whether that data would ever see the light of day. Qantas, at the time, reassured customers that sensitive credentials like passwords, login tokens, and card data […]

Are identity tools failing SOC operations?
Data security breaches aren’t slowing down. From exposed AWS buckets to credential-stuffing attacks on SaaS platforms, compromised identities remain the weakest link in enterprise security. According to Verizon’s 2025 Data Breach Investigations Report, stolen credentials were the initial entry point in 22% of breaches, and a staggering 88% of basic web application attacks involved the […]

How to mitigate the security risks of frontline SaaS apps
A digital transformation is taking place on the frontline. Employees who were once underserved by enterprise technology are now gaining access to modern SaaS tools that drive efficiency, collaboration, and real-time decision-making. For organizations, it’s a powerful opportunity to unlock greater productivity at scale. But it also introduces new risks. Each new endpoint expands the […]
Allianz Life data breach impacts 1.4 million customers
Allianz Life has announced it suffered a data breach that impacted the personal data of the majority of its 1.4 million customers. The company, a major provider of life insurance and annuities, is part of Allianz SE—one of the world’s largest financial services groups, serving more than 128 million people globally. Here’s everything we know […]
AI grounding: How to achieve it
You’ve rolled out a generative AI tool to help teams move faster and work smarter. But there’s a problem: the answers are off…Sometimes outdated…Sometimes just plain wrong. That’s what happens when AI isn’t grounded—when it doesn’t have access to the right internal data. Instead of insights, you get hallucinations. And it’s a major issue. In […]

Do you need cyber insurance in 2025?
We’re only halfway through 2025, and there have already been over 12,000 publicly disclosed data breaches. From small brick-and-mortar businesses to multinational tech companies, it’s clear that no organization is immune to a cybersecurity incident. Preparation is key—and one increasingly vital part of shoring up against cyber-attacks is cyber insurance. In this article, we’ll explore […]
Secure AI usage: Why policies aren’t enough
Every organization understands that AI is central to competing and thriving in the future of work. But with that opportunity comes risk. For every gain in speed, efficiency, and output, AI introduces new vulnerabilities: data leakage, regulatory exposure, ethical concerns, and the potential misuse of sensitive information. Governing this technology is critical to long-term success. […]
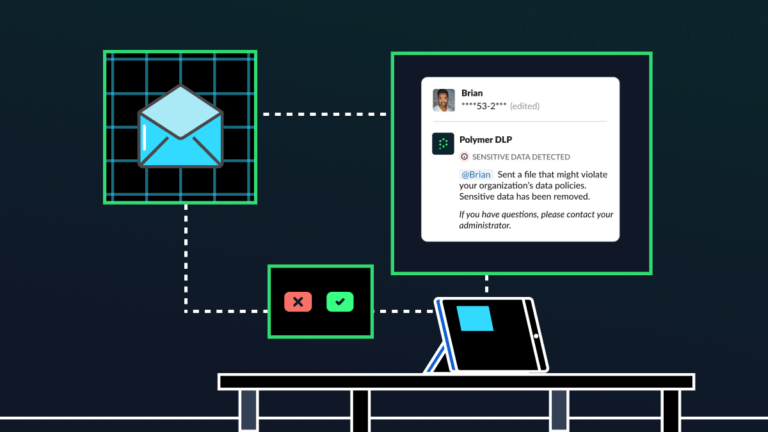
Human risk management: The key to a culture of cybersecurity
All employees make mistakes—whether that’s a typo in an email, sending a document to the wrong person or missing a deadline. Some mistakes, though, have greater consequences than others, especially when it comes to cybersecurity and compliance. Sending a sensitive document to the wrong recipient, for example, can be an immediate data breach and compliance […]
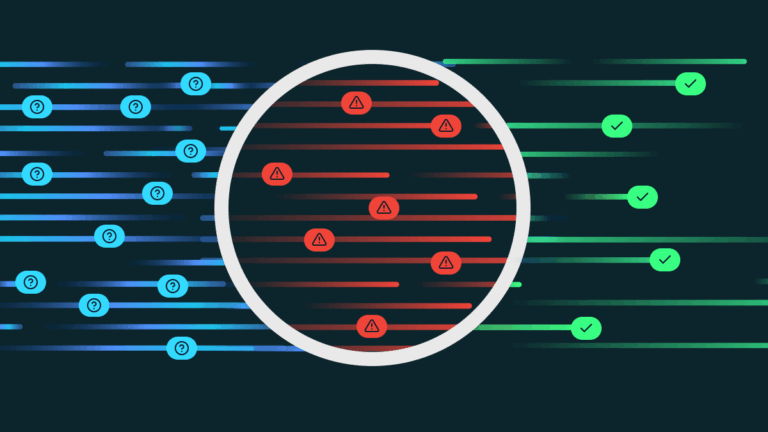
Runtime data security vs DSPM
In the alphabet soup of cloud security tools, few acronyms have risen faster—or with more promise—than data security posture management (DSPM). Touted as a cure-all for sensitive data exposure, DSPM promises deep visibility into cloud environments. But as many CISOs have found, visibility alone isn’t enough. DSPM might show you where the problems are—but it […]