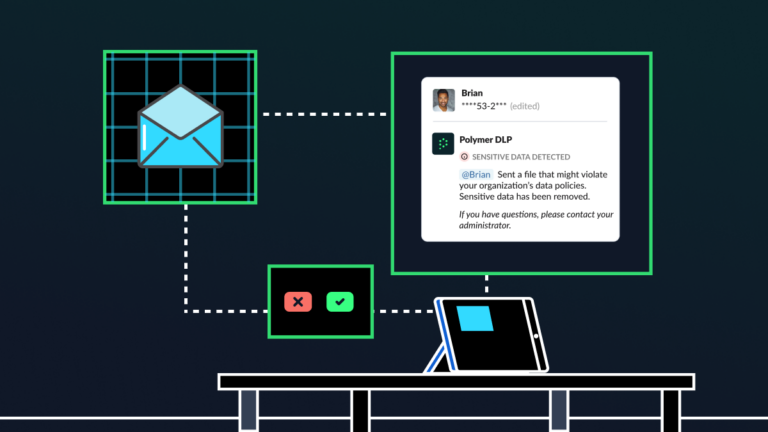
Security awareness training is often seen as the cornerstone of managing the human factor. The goal is simple: provide employees with enough information to recognize and avoid potential risks. These programs can take many forms, from posters that offer cyber hygiene reminders to more structured eLearning sessions designed to ensure every employee has completed necessary […]

Disney quits Slack after data breach
Disney is set to abandon Slack following a significant data breach that occurred in July, which exposed over 1TB of confidential messages and files from the company’s internal communication channels. Internal emails shared reveal that Disney has commenced the transition to new “streamlined enterprise-wide collaboration tools,” with plans to complete the migration by the end […]

AT&T fined $13M by FCC for supply chain data breach
The Federal Communications Commission (FCC) has imposed a hefty $13 million fine on AT&T following a cloud security lapse that resulted in a data breach last year, compromising the personal information of 8.9 million customers. In an unusual twist, the breach didn’t originate within AT&T itself but rather stemmed from a security incident involving one […]
Payment gateway data breach: 1.7 million credit card owners affected
Payment gateway provider Slim CD has revealed a significant data breach affecting approximately 1.7 million people, compromising sensitive credit card and personal information. In a letter sent to affected clients, Slim CD admitted that cybercriminals had access to its network for an extended period, spanning from August 2023 until June 2024. This means that hackers […]
AI spoofing: What it is and how to spot it
Cloud account hijacking and spear-phishing emails have long been a concern amongst corporate security teams. Even with tools like multi-factor authentication and spam filters, malicious actors often uncover ways to either break into employee cloud accounts and attempt to persuade unwitting users to share sensitive details. Thankfully–up until now–there’s usually been a few tell-tale signs […]

SaaS security best practices: the ultimate guide
In this guide, we’ll explore the best practices for securing SaaS applications, from understanding key threats and the vendor landscape to building a culture of data protection. By delving into the nuances of SaaS security, you’ll be better equipped to navigate the complex landscape of cloud-based threats and maintain robust defenses against potential vulnerabilities. What […]

National Public Data breach: 3 million records leaked
Nearly 2.7 billion records containing personal information of individuals in the United States were leaked on a hacking forum, exposing sensitive data such as names, social security numbers, all known physical addresses, and potential aliases. Here’s what we know so far. National Public Data: Background The data reportedly originates from National Public Data, a company […]

Machine learning: the secret to effective data loss prevention
Data loss prevention (DLP) has a noise problem. Despite security teams carefully programming their solutions to catch sensitive data, most DLP tools alert them to benign instances—and lots of them. The reason? Regular expressions. Once the cornerstone of DLP, regular expressions have become outdated for the modern, cloud-based world. They cause inconsistent, inconsequential, inordinate amount […]

Everything you need to know about LLM DLP
Large language models (LLMs) are rapidly reshaping the workplace—tools like ChatGPT are revolutionizing marketing, while AI-driven predictions are transforming healthcare. The benefits are significant, but so are the risks. LLMs thrive on data, analyzing, logging, and storing every piece of information your employees share within their expansive neural networks. You might assume your current data […]
Anatomy of the CrowdStrike outage: Lessons learned
Last Friday, a wave of digital disruptions swept across the globe as Microsoft users found themselves facing an unexpected and severe issue: their computers simply refused to power on. This seemingly small glitch spiraled into a global crisis, causing major television networks to go dark, disrupting air travel with mass flight cancellations, and forcing countless […]

Are malicious insiders lurking in your SaaS apps?
The recent Disney data breach highlights the ever-present risk malicious insiders present to organizations–especially in the cloud-based working world. Whether on Microsoft Teams, Slack, or Google Workspace, almost all employees now rely on SaaS apps to carry out their work. In the process, they’re sharing, uploading, and downloading plenty of workplace data. For the most […]