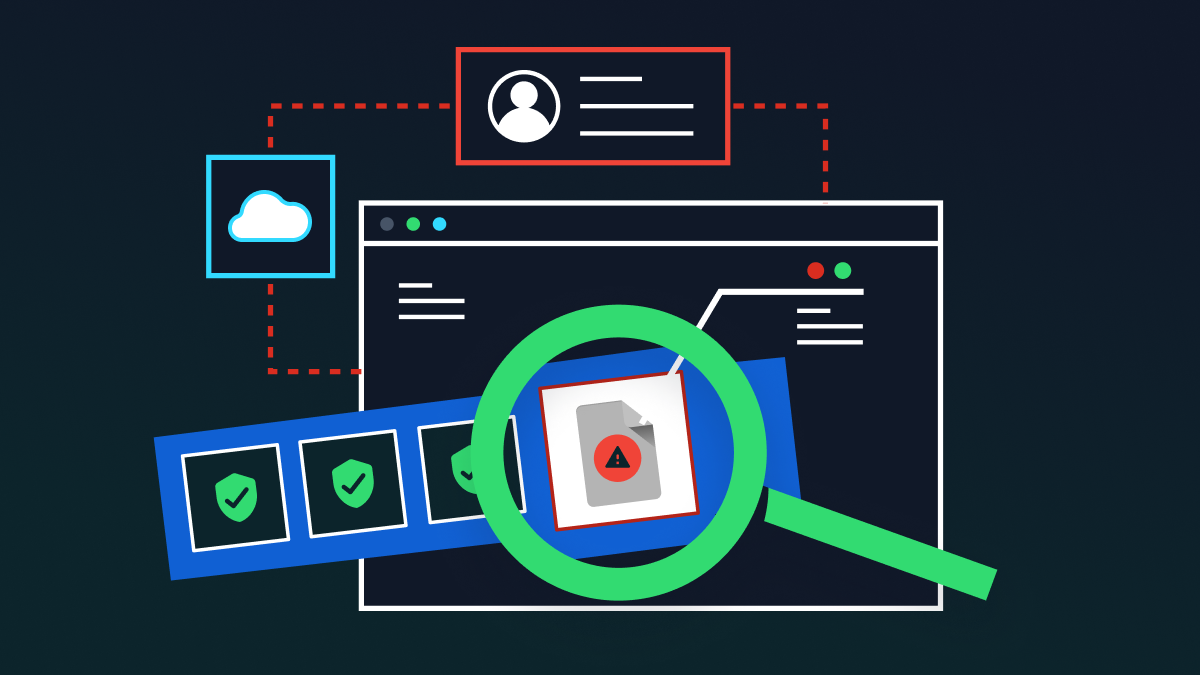
Document-based malware is pretty common these days.
An email analysis by Barracuda Networks revealed malware hidden in documents accounts for over 50 percent of all malicious files.
This trend appears to be gaining momentum as cyber crooks continue to spam documents, according to WatchGuard, a tech security company.
While these documents look legit, they come packed with code that can potentially put your organization at risk.
Malware inserted into documents is particularly sneaky for two reasons.
First, cybercriminals use social engineering tricks to make you think you’ve received a legit file from a person you know, such as trading partners or friends, when in reality, you haven’t.
On top of that, the malware camouflages in file types you’re familiar with and would ordinarily trust, such as Microsoft Office programs.
How does document-based malware work?
The malware embeds malicious codes into documents, PDFs, spreadsheets, and other files.
Once on your computer, it can perform various malicious tasks such as stealing passwords or infecting your email contacts.
The malware replaces ordinary commands with malicious code. The worst part is that you can activate the malware through normal day-to-day tasks such as opening your emails or editing Word documents.
Document-based malware overrides your commands, altering your computer, causing damage, and further spreading the malicious code.
Often, the malware tampers with word processors by adding, deleting, and changing words within your documents.
Further, it moves text, adds images, and corrupts your hard drive. In addition, it can infiltrate your email, sending unsolicited emails to your contact list. Unsuspecting recipients will open your emails in good faith, spreading the virus into their computers.
Archive and script files are also a common method for distributing attachment-based malware.
How to know If your computer has document-based malware
You may not know if your computer is infected with malware inserted into documents.
Some signs to look out for include:
- Strange formatting in your documents
- New files you haven’t created
- Altered or deleted text
People in your email contact list may also email you notifying you of the unusual email they’ve received from your account. In most cases, these emails contain odd wording or formatting, with a suspicious attachment included.
How to prevent and block malware attack
Modern malware attacks are sophisticated and encrusted, which means organizations must invest in the right systems to detect and block them.
To stay safe, organizations need to use the following securing technology.
Phishing-detection systems
Investing in a reliable phishing detection system and related security software can help identify even the slightest of clues and prevent potentially malicious messages and attachments from reaching your email boxes.
Blacklisting
Cybercriminals and spammers use their own infrastructure. This implies they use the same IP address long enough to enable security software to blacklist and detect them. The software can then blacklist the IP address once it is apparent the address is sending a significant volume of spam.
Advanced firewalls
An advanced network firewall can help analyze malware if a user clicks a link that initiates a download or malicious attachment. The firewall allows you to intercept possible attacks by flagging malware that attempts to infiltrate your system.
Malware detection
Software that runs on dynamic and static analysis can detect a document attempting to start an unsolicited download from the internet.
Threat intelligence systems can flag the web address while providing analysis to enable you to know if the document is malicious.
Next-gen data loss protection
Current DLP solutions are failing to keep up with the latest iterations of Malware. Modern DLP solutions like Polymer can do a better job of malware detection and blockage.
The bottom line
No computer is safe from malware inserted into documents.
There’s every probability that a user can download malicious documents through email or send them via SaaS platforms such as Slack or Zendesk, putting your organization at risk.
Polymer security scans for SaaS can help protect your organization from document-based malware by running thorough system scans. And the beauty of it is that Polymer scans your scans in minutes.