Secure AI workflows at runtime
The platform to identify, analyze, and mitigate real-time security risks across your AI and SaaS ecosystem.
LEADING ORGANIZATIONS TRUST POLYMER

Respond to the new AI threat vector
AI agents work alongside your employees in the tools they use every day.

Polymer secures data the moment it’s generated or accessed by AI or humans.
Identity-aware detection & response
Create and manage context-driven security policies tailored to your organization’s unique requirements and AI usage.
Manage employee & AI access
Group human and non-human identities to control how they can interact with data.
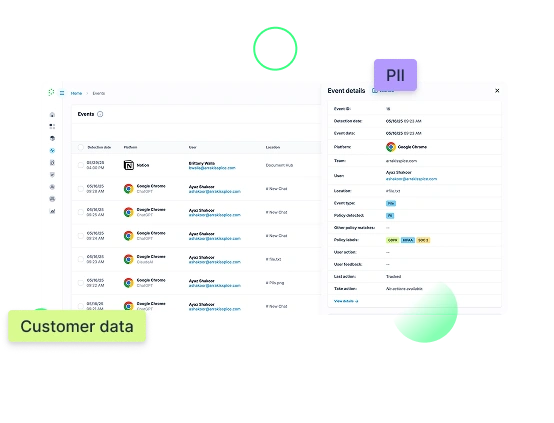
Detect, classify, & label data
Continuously monitor data in motion and at rest based on your custom security policies.

Quantify risk
Assess reports and risk scores to expose vulnerabilities such as shadow AI usage, insider threats, and misconfiguration.
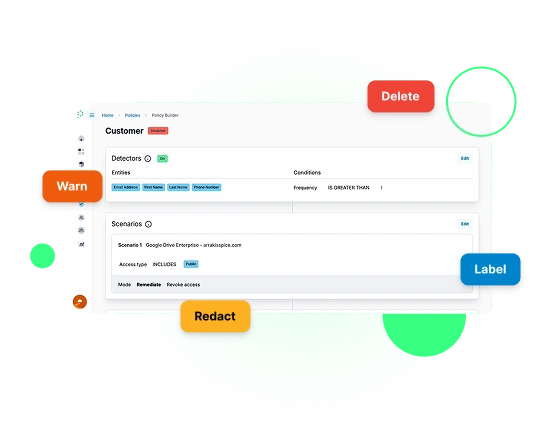
Automate policy enforcement
Remediate violations at runtime: redact sensitive data, revoke file access, and trigger custom workflows with or without human review.
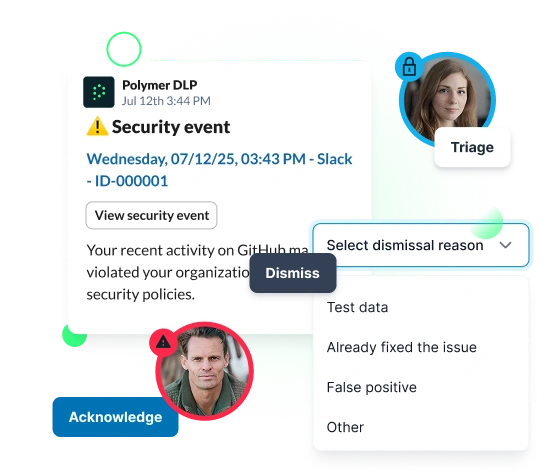
Scale security operations
Make your employees part of the solution with real-time training and response that enable business.
Demonstrate continuous compliance
Generate audit logs mapped to regulatory frameworks such as HIPAA, SOC 2, CCPA, and GDPR.






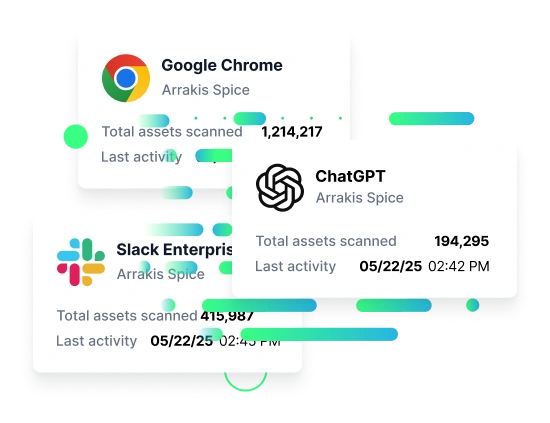
Built for enterprise scale
Every day Polymer scans and secures millions of data assets across AI and SaaS ecosystems.
End users
Assets scanned
Global IDs supported
Enterprise-ready AI & SaaS security

Cloud or self-hosted single tenant deployment

Seamless integration in your existing tech stack

Role-based access controls (RBAC)

SOC 2 Type II compliant

Polymer provides us with the flexibility to effectively manage compliance and security parameters, offering unparalleled protection of our customer’s PII data.
John Storozuk
Security Partner, ClickUp

Polymer saves us time and money in satisfying our SOC 2 ongoing monitoring and data privacy guidelines.
Michael Cramer
Head of Product, Routefusion

Our prior solution required 8 hours per week of FTE time to manage alerts. With Polymer, we are down to 0.
Mark Magpayo
Sr. Director of Security Operations, Signify Health

Polymer is giving us 99% accuracy in sensitive data found over SaaS.
Dave Bour
Director of IT & Information Security, Medly
Data security resources

Millions of Instagram accounts subject to potential data breach
In early January 2026, millions of Instagram users around the world woke up to unrequested password reset emails. This wave of...
Update: LastPass fined £1.2 Million: A costly reminder to strengthen security
The UK Information Commissioner’s Office (ICO) has fined LastPass £1.2 million for security failures tied to its 2022 breach—nearly...

How email became the weakest link in enterprise security
If you wanted to steal from a company today, you wouldn’t start in the data lake—you’d start in the inbox. Email is where work...



