Cloud-hosted products come with data exfiltration risks that are not well understood. This has definitely been heightened by remote teams and haphazard cloud adoption during COVID-19. Today’s IT teams face a multitude of cloud security challenges: managing remote access to applications; preventing data leakage, ensuring users are who they see are; watching for malware and more.
The cloud access security broker (CASB) concept was designed to solve just these challenges. However the promised land pitched by CASB firms never quite came to fruition due to the operational inefficiencies inherent in most tools.
What is CASB?
Gartner defines CASBs as “on-premises, or cloud-based security policy enforcement points, placed between cloud service consumers and cloud service providers to combine and interject enterprise security policies as the cloud-based resources are accessed.”
Simply put, a CASB is kind of like the bouncer at an exclusive party. The party is your cloud applications, and the queues of people lining up to get in are your employees – and possibly some cyber-attackers. It’s the bouncer – CASB’s – job to check everyone at the door, ensuring that only people who have been invited get into the party. It’s also their job to check that people aren’t bringing anything dangerous – aka malware – inside, or stealing anything when they leave, such as sensitive corporate data.
In the beginning, CASBs were deployed as physical appliances in data centers. CASB architecture has evolved overtime; it has moved to become a cloud service itself, frequently referenced to within the security-as-a-service bracket. CASBs have also moved from proxies to more commonly using APIs. This is because proxies have a security disadvantage: they can’t see traffic unless this traffic is aligned to a specific handle.
Using a proxy is like having a bouncer at the front door of your party, but no one checking the walls and the back gate. APIS, on the other hand, secure both managed and unmanaged traffic, ensuring no security gaps. Going back to the bouncer analogy, APIs are like having security guards on every potential entrance and exit point to your cloud applications.
Why CASB matters
The average organization uses over 1,000 cloud applications and one out of five files uploaded to the cloud contain sensitive information. Keeping track of who is using these apps, what they are accessing and how they are using sensitive data is an almost impossible task for IT teams – unless they have a CASB.
At the core of CASBs is much needed visibility into cloud applications, data and users. 80 percent of employees admit to using personal mobile devices for work purposes. Employees accessing applications from these devices, plus potentially unsecure networks, is a huge security risk. A CASB mitigates this risk, by shining a light on, and managing, shadow IT access.
The solution is also beneficial for compliance, data protection and threat prevention. GDPR fines have cost organizations an extraordinary total of $1.3 billion since 2019. Many of these incidents have resulted from credentials theft or improper access controls to cloud environments, leaving sensitive data exposed. In fact, an estimated 80% of security breaches involve stolen credentials. CASBs help through auditing, monitoring user behavior and data loss prevention to prevent this.
What makes CASB different from other web security applications?
With a myriad of web security applications out there, it can be difficult for organizations to understand what they need, and how these solutions differ from each other.
So, let’s take a look at how CASBs compare to the most common web security technologies.
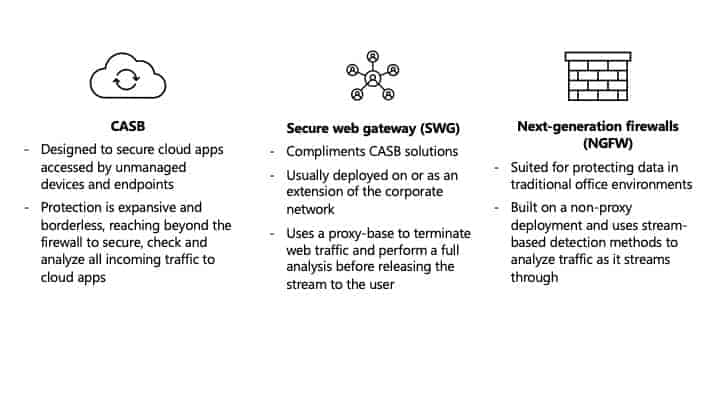
1. CASB
Modern CASBs are designed to secure cloud apps accessed by unmanaged devices and endpoints. Their protection is expansive and borderless, reaching beyond the firewall to secure, check and analyze any and all incoming traffic to your cloud applications.
2. Secure web gateway (SWG)
SWGs compliment CASB solutions, but how they help organizations is completely different. SWGs are an evolution of next-generation firewalls (more on that below!). They are usually deployed on or as an extension of the corporate network. They offer perimeter protection, filtering in-bound threats and web traffic. These solutions usually use a proxy-base to terminate web traffic and perform a full analysis before releasing the stream to the user. This gives the organization granular control of traffic – but its capabilities only extend to the perimeter.
3. Next-generation firewalls (NGFW)
NGFW are more similar to SWGs. These solutions are best suited for protecting data in traditional office environments, where there are managed endpoints and premises-based infrastructure. NGFWs are built on a non-proxy deployment and use stream-based detection methods to analyze traffic as it streams through. However, unlike CASBs, these solutions are unable to monitor and protect unmanaged endpoints and devices.
As you can see from a quick overview of each solution, the differences are vast. While SWG and NGFW focus on perimeter protection, CASBs focus on data protection. The solutions compliment each other. For total protection, it’s advised organizations use a combination.
How to choose the right CASB solution
Now you’re convinced your organization needs a CASB, it’s time to choose the right one. Not all CASBs are created equal. Here are key features to look for:
1. Identify the five most critical cloud applications used by your organization.
2. Limit your CASB options to those that offer API support for these cloud apps.
3. Next, determine if the CASB will be integrated with your existing IAM or SSO systems (make sure to define these terms). If so, you can narrow down the choices to those that support such integrations.
4. Choose the CASB deployment mode that best suits your organization:
· Forward proxy: These architectures work by installing an agent on all employee devices, in order to gain visibility into how cloud applications and data are being used.
· Reverse proxy: Unlike forward proxies, these have an agent-less architecture. They are deployed in the cloud and act like a gatekeeper to these services, rather than securing devices. However, as mentioned earlier, proxy-based CASBs run into issues and often miss users who aren’t configured to access cloud services through them.

· API control: APIs are the most advanced form of CASB. They are out-of-band solutions that integrate into cloud services, providing security and monitoring by maintaining a dialogue with other known APIs.
These deployment modes are important to take into account, as some vendors only support specific deployments. For example, Cisco and Savyint only support API control.
5. Determine if the choices can be integrated with other critical software, such as application firewalls, SWG, and data loss prevention software.
6. Perform a cost/benefit analysis of the remaining CASB contenders, and choose the one that best fits your specific needs and budget.
Conclusion
In today’s decentralized, cloud-driven work environment, CASBs are an important tool for securing data. As more and more employees use their own devices for work and cloud applications continue to proliferate, CASBs provide a much-needed means to gain control of shadow IT.
Plus, with cyberattacks constantly increasing, these solutions are an important part of meeting compliance standards, preventing data loss and securing sensitive data from hackers.
The trick with CASBs is to find the right one. Your organization needs more than just one bouncer at the front door. You need an army of data protectors, who will secure your cloud applications from all angles, like Polymer DLP.



