The world of work is constantly changing. If you look back at the last 20 years, you’ll realize by just how much. Fax machines, file cabinets and long days in the office are mostly a thing of the past. Now, people work from anywhere, on any device, at any time.
Technology, of course, is the driving force behind these new workplace capabilities. Employees now have the hardware and software to do their jobs from wherever they are. However, with new opportunities always comes challenges. And the biggest one since the dawn of the work-from-anywhere world is most certainly cybersecurity.
As we all know, the pandemic accelerated the shift towards a hybrid work environment. Most companies weren’t able to embrace remote work strategically. It was a haphazard, “do it now” kind of operation. Consequently, many organizations are now trying to plug security gaps leftover from the last crazy 18 months.
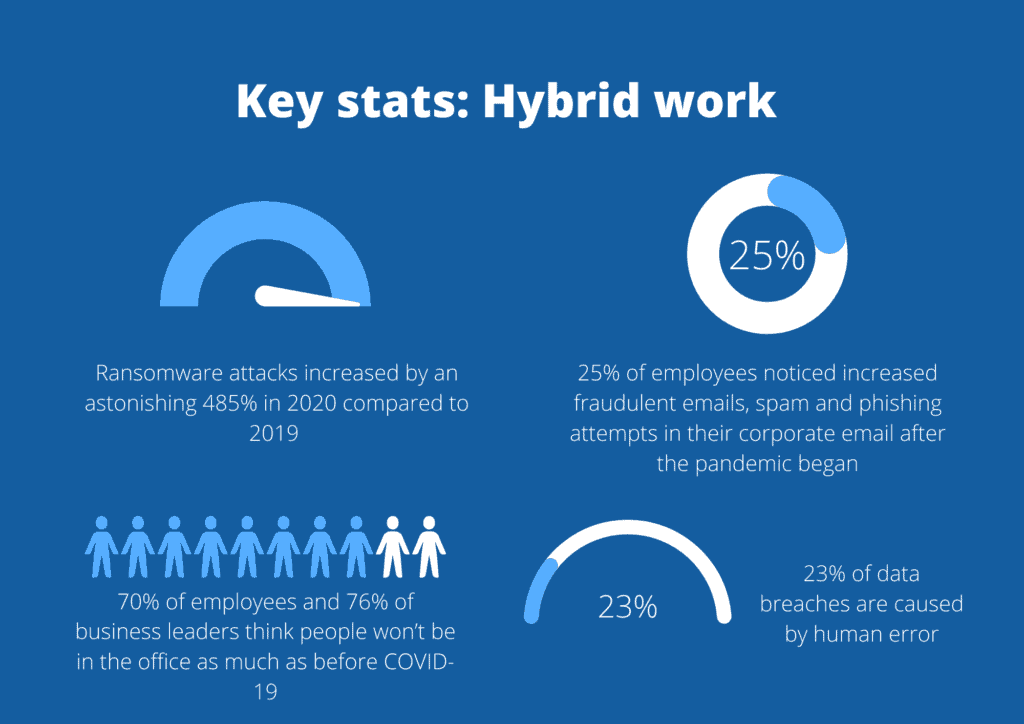
It’s not a case of going back to how things were before either. BBC research on the future of work found that 70% of employees and 76% of business leaders think people won’t be in the office as much as before COVID-19. The only way is forward, not backwards. But, moving forwards need to be just as much about security as it is productivity and efficiency.
The security risks of a hybrid environment
For a business leader, the term “data breach” is enough to send a shiver down the spine. Over the last decade, we’ve seen countless brand names splashed across the headlines for losing customer data, followed quickly at the heels by class-action lawsuits, compliance fines and, in the worst-case scenario, brands going bust.
The hybrid environment, if not properly secured, is a data breach waiting to happen. Gone is the traditional ‘castle and moat’ approach that kept data safe. Now, organizations need to adapt to the fact that employees will access data from all over the place. This presents several challenges:
- The risk of human error: 23% of data breaches are caused by human error, according to IBM’s Cost of a Data Breach report. Unfortunately, this risk is inevitable. Employees are not security experts. Someone will always use a weak password, accidentally click a phishing link or ignore software updates.
- Malicious outsiders: Some cybercriminals are exceptionally savvy. They know that employees are working from home – and they want to find the weak link that will let them into your company. Deloitte found that one quarter of all employees noticed increased fraudulent emails, spam and phishing attempts in their corporate email after the pandemic began.
- Poor network security: Home network environments are rarely as secure as office ones. Without the protection of corporate firewalls and blocked IP addresses, employees are more vulnerable to cyber-attacks.
- Shadow IT: Cloud-based applications are the backbone of remote work productivity. However, not every app that employees use is sanctioned by the IT team. Without you realizing, your employees are likely logging into – and sharing data with – several unknown applications, putting sensitive data at risk.
Despite these challenges, we’re definitely not saying that organizations should shy away from hybrid work. For competitiveness, productivity and company culture, this new working environment is definitely the way to go. Companies need to learn to secure the hybrid environment properly.
Wait…what about VPNs?
VPNs were a life-saver for many organizations at the start of the pandemic. They were the go-to tool to facilitate remote working. While VPNs certainly have their place in a hybrid security model, they aren’t the be-all and end-all. These tools tend to suffer from security erosion. This means that, as they become over-provisioned, they depreciate and become less effective. As well as this, VPNs can often hamper productivity due to strict security policies, which aren’t flexible enough to adapt to the pace of enterprise change.
So, while VPNs are a handy tool, for now, they aren’t the future. By contrast, the future blends security with the user experience, ensuring that employees and security teams can be productive without putting the other at risk. This is where zero trust becomes pivotal.
What is zero trust?
At its most simple, zero trust is an approach to security based on the idea of “trust no one, verify everyone.” It is a perimeter-less form of protection, focused less on where users log on from and more on who the user is.
Zero trust isn’t one solution or technology; it’s more of a strategy: an overarching aim for security that you can achieve by tailoring your current security solutions, company policies and workplace culture.
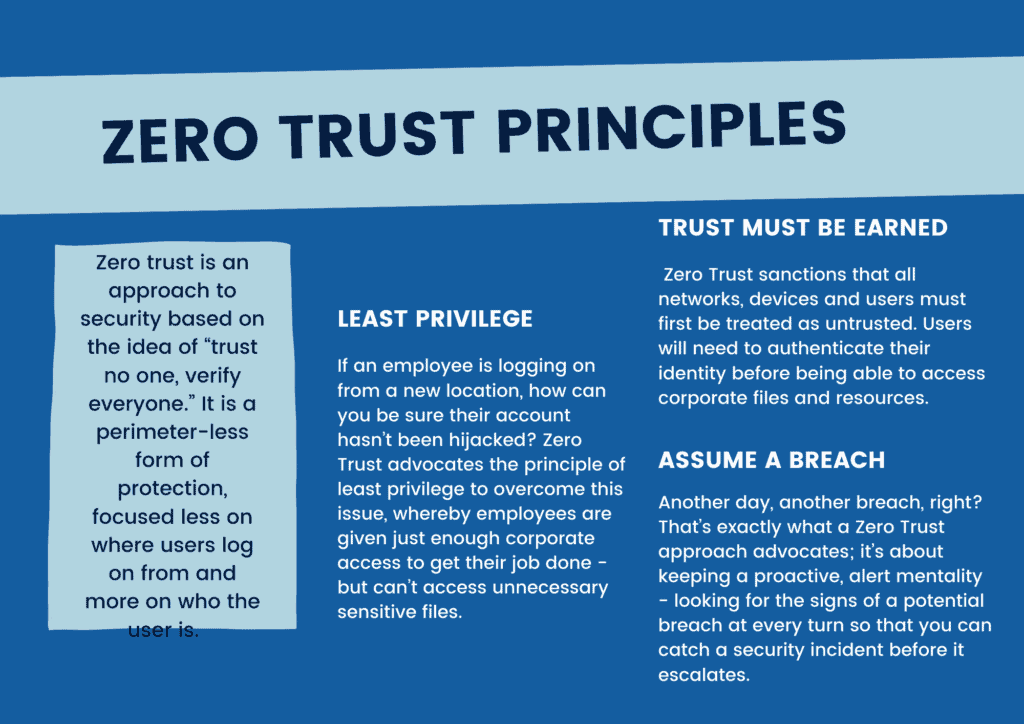
Trust must be earned: Zero Trust sanctions that all networks, devices and users must first be treated as untrusted. Users will need to authenticate their identity before being able to access corporate files and resources.
Least privilege: If an employee is logging on from a new location, how can you be sure their account hasn’t been hijacked? Zero Trust advocates the principle of least privilege to overcome this issue, whereby employees are given just enough corporate access to get their job done – but can’t access unnecessary sensitive files.
Assume a breach: Another day, another breach, right? That’s exactly what a Zero Trust approach advocates; it’s about keeping a proactive, alert mentality – looking for the signs of a potential breach at every turn so that you can catch a security incident before it escalates.
Benefits of zero trust security
Any organization that takes a holistic zero trust approach to security will drastically reduce their chances of a data breach. Because zero trust assumes a breach and forces users to earn trust, it reduces the risk of data leakage and exfiltration.
Moreover, with a zero trust architecture, security policies are tied to the identity of users and workloads. This allows security to travel with assets, enabling security teams to gain better visibility and control of data as it moves in and out of cloud environments and different applications. In line with this, zero trust can also improve compliance with critical regulations like the GDPR, PCI DSS and HIPAA.
Away from just security, though, zero trust also has benefits from an operational perspective. It has the potential to put the power back in the hands of IT teams, giving them a true sense of their security posture and maturity.
Three steps to starting with Zero Trust
Without a doubt, zero trust is the future of security. But creating an end-to-end zero trust architecture takes time, investment and a wide array of skills. In other words, adopting zero trust isn’t an overnight story. But, you can get started today. Here’s how:
Step 1: Identify your users
Zero trust begins with an understanding of your company’s user base. To enforce zero trust without hindering productivity, you should implement tools like Identity and Access Management with single sign-on. You should ensure that only users who are verified through these tools can access corporate data and applications.
Step 2: Protect your data
Just because a user has verified access to corporate data, that doesn’t mean they should be fully trusted. This means that as well as authenticating users, additional steps should be taken to prevent accidental data loss or data exfiltration. Utilizing a cloud-based DLP solution, or Cloud Access Security Broker, provides real-time visibility into how users are interacting with sensitive data. As well as visibility, these solutions also use pre-defined policies to prevent data from being unlawfully shared or moved.
Step 3: Include cloud applications
Collaboration tools like Slack, Box and Outlook should all be considered within the Zero Trust model. Security controls, including DLP and user behavior monitoring, should extend to these cloud applications, where it is extremely common for data leakage to occur. For example, using data redaction, a next-gen DLP solution can prevent an employee from using Slack to share sensitive data with an unauthorized user in real-time.
If you’re concerned about overhauling legacy systems in favor of a Zero Trust architecture, then we recommend you start with a next-generation, cloud-based DLP solution – like Polymer.
These solutions are built on a Zero Trust framework. They incorporate security features such as identity and access management and data protection and redaction in cloud applications to prevent unauthorized or suspicious users from misusing sensitive data.