The cloud storage service Dropbox is used by over 17.2 million individuals and organizations worldwide. This SaaS platform makes it easy to store, manage, and collaborate on documents from anywhere, on any device. However, despite its popularity, Dropbox has a checkered past when it comes to data privacy and security. Here, we’ll look at Dropbox’s […]

Is Notion secure? What you need to know about Notion vulnerabilities
In the eight years since it launched, Notion has become a much-loved collaboration and productivity tool used by enterprises large and small across the globe. Because it’s intuitive to use, cloud-based and brimming with helpful features, many employees rely on Notion for tasks like note taking, sharing documents, project management and database storage. But, despite […]

The department of defense presses the accelerator on CMMC 2.0
On December 26, 2023, the department of defense (DoD) announced the proposed rule for CMMC 2.0, which is open for comments until February 26, 2024. If you’re an organization that works with the DoD, it’s time to start preparing for CMMC 2.0 compliance. What is the difference between CMMC 1.0 and CMMC 2.0? In 2020, […]

Over 4 million sensitive school records exposed in cloud data leak
This week, thousands of schools across the US became embroiled in a mass data leak, after the school safety software company—Raptor Technologies—accidentally left troves of sensitive data exposed on the internet. What happened with the Raptor Technologies data breach? On January 11, a cybersecurity researcher unearthed a concerning discovery: an unprotected database housing an estimated […]
Need to know: NIST’s upcoming guidance on cybersecurity awareness & training
It’s been 20 years since the National Institute of Standards and Technology (NIST) released its guidance on building enterprise security awareness and training programs. A lot has changed since then. With new attack types, the advent of cloud applications, the work-from-anywhere era, and generative AI, NIST has realized that their previous idea of effective training […]

Shadow AI: The new shadow IT threat vector
While major corporations such as Apple, Spotify, and Samsung are all placing restrictions on how employees interact with generative AI in the workplace, it appears that many workers are going full steam ahead with AI use. Recent research by Dell, for example, shows that 91% of respondents have used generative AI, and a notable 71% […]
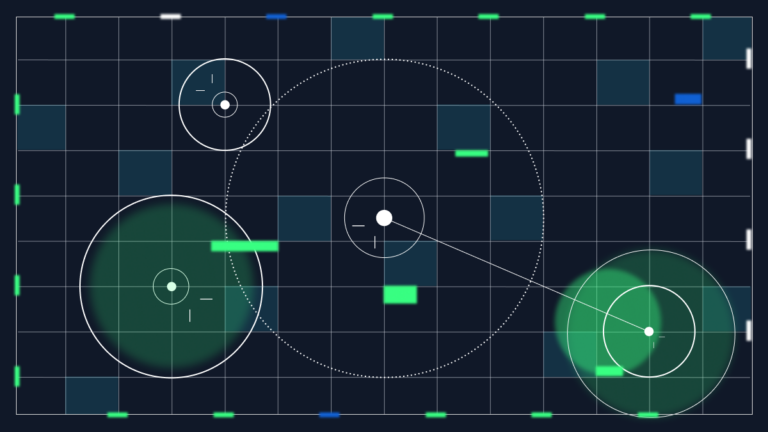
Noisy DLP? Regular expressions are probably to blame
Ask any security professional what their biggest headache is with data loss prevention (DLP) solutions, and you can bet they’ll say: false positives. Erroneous noise, which happens when a policy is triggered by mistake, has become all too common. Plus, every alarm needs to be investigated, meaning these noisy solutions drastically harm productivity in the […]
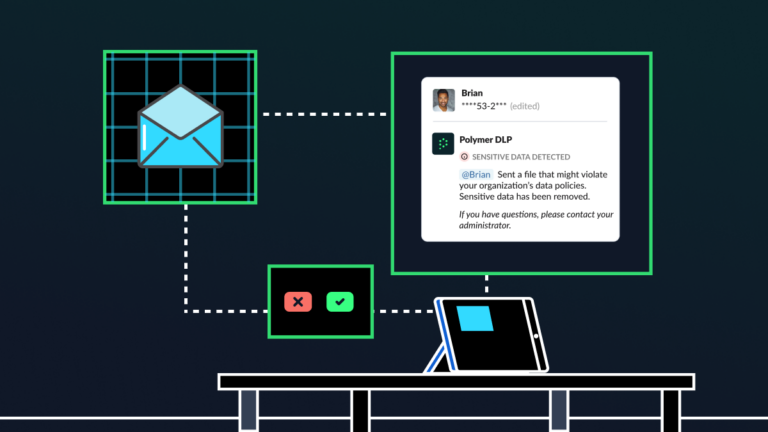
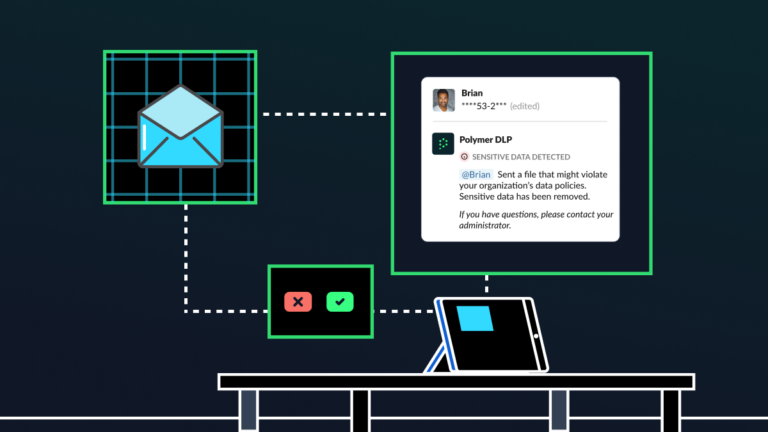
Are your customer service agents being exposed to sensitive customer data?
Customer service teams are often the first point of call for your customers. Armed with tools like Zendesk, Salesforce, HubSpot, OneDrive, Kustomer, and more, they’re on the front lines, tackling order disputes, service issues, inquiries, and account updates. Beyond that, they also play a vital role in upholding cybersecurity. While they’re certainly not expected to […]

What are the risks of using AI in the software development life cycle?
Authors: Yasir Ali (Founder, Polymer DLP) & Aaron Bray (Founder, Phylum) Software supply chain is at risk with LLM adoption Developers now have access to powerful generative AI models that assist in writing code, automating mundane tasks, and improving productivity. While this technology holds tremendous promise, it also brings to light a pressing concern—the potential […]

What’s the difference between DSPM & CSPM?
Not too long ago, cloud security posture management (CSPM) seemed like the holy grail of cloud security, promising unparalleled protection in the cloud-first world. However, organizations have come to realize that although CSPM is great at identifying infrastructure vulnerabilities, data breaches are still happening troublingly frequently. As a result, data security posture management (DSPM) has […]

FISMA compliance: a comprehensive guide
The Federal Information Security Management Act (FISMA) is a United States federal law enacted in December 2002 under the E-Government Act. The act mandates federal agencies to develop, document and implement an information security program, considering both processes and systems controls, to “protect information and information systems from unauthorized access, use, disclosure, disruption, modification, or […]


